Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Validated and proven Cisco 300-215 exam questions help you pass the Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR) exam – a reliable 300-215 dumps by Pass4itSure.
Click https://www.pass4itsure.com/300-215.html (300-215 PDF + 300-215 VCE) live updates, 100% correct exam questions and answers, to help you pass the exam 100%.
Free download Cisco 300-215 exam PDF
Download Cisco 300-215 PDF https://drive.google.com/file/d/1cDU5zaxAoL8pknlGNiJyJj797KbiAqvX/view?usp=sharing
The latest free Cisco 300-215 exam PDF QAs is a dumps from Pass4itSure 300-215!
Is there a free Cisco 300-215 exam practice question for me to learn
You’re right, here you can get some valid Cisco 300-215 exam practice questions for free. Shared by Pas4itSure 300-215 dumps. Complete 300-215 questions and answers you also need to access Pass4itSure.com.
Latest Cisco 300-215 practice test for free
QUESTION 1
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named
parsed_host.log while printing results to the console?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
QUESTION 2
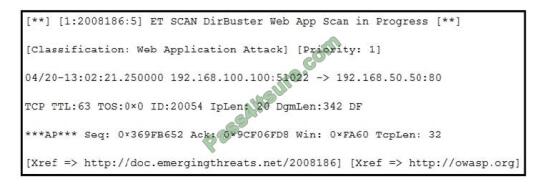
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?
A. brute-force attack against the web application user accounts
B. XSS attack against the target webserver
C. brute-force attack against directories and files on the target webserver
D. SQL injection attack against the target webserver
Correct Answer: C
QUESTION 3

Refer to the exhibit. After a cyber-attack, an engineer is analyzing an alert that was missed on the intrusion detection
system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability.
Which two migration techniques should the engineer recommend? (Choose two.)
A. encapsulation
B. NOP sled technique
C. address space randomization
D. heap-based security
E. data execution prevention
Correct Answer: CE
QUESTION 4
An organization uses a Windows 7 workstation for access tracking in one of their physical data centers on which a
guard documents the entrance/exit activities of all personnel.
A server shut down unexpectedly in this data center, and a security specialist is analyzing the case. Initial checks show that the previous two days of entrance/exit logs are missing, and the guard is confident that the logs were entered on the workstation.
Where should the security specialist look next to continue investigating this case?
A. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon
B. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\ProfileList
C. HKEY_CURRENT_USER\Software\Classes\Winlog
D. HKEY_LOCAL_MACHINES\SOFTWARE\Microsoft\WindowsNT\CurrentUser
Correct Answer: A
Reference: https://www.sciencedirect.com/topics/computer-science/window-event-log
QUESTION 5
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During
the incident, members of the security team failed to report the abnormal system activity due to a high project workload.
Additionally, when the incident was identified, the response took six hours due to management being unavailable to
provide the approvals needed.
Which two steps will prevent these issues from occurring in the future? (Choose two.)
A. Introduce a priority rating for incident response workloads.
B. Provide phishing awareness training for the fill security team.
C. Conduct a risk audit of the incident response workflow.
D. Create an executive team delegation plan.
E. Automate security alert timeframes with escalation triggers.
Correct Answer: AE
QUESTION 6
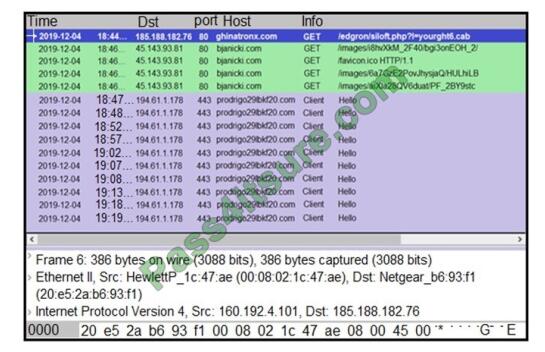
Refer to the exhibit. A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the
initial Ursnif banking Trojan binary to download.
Which filter did the engineer apply to sort the Wireshark traffic logs?
A. http.request.un matches
B. tls.handshake.type ==1
C. tcp.port eq 25
D. tcp.window_size ==0
Correct Answer: B
Reference:
https://www.malware-traffic-analysis.net/2018/11/08/index.html
https://unit42.paloaltonetworks.com/wireshark-tutorial-examining-ursnif-infections/
QUESTION 7
A security team receives reports of multiple files causing suspicious activity on users\’ workstations. The file attempted
to access highly confidential information in a centralized file server. Which two actions should be taken by a security
analyst to evaluate the file in a sandbox? (Choose two.)
A. Inspect registry entries
B. Inspect processes.
C. Inspect file hash.
D. Inspect file type.
E. Inspect PE header.
Correct Answer: BC
Reference: https://medium.com/@Flying_glasses/top-5-ways-to-detect-malicious-file-manually-d02744f7c43a
QUESTION 8
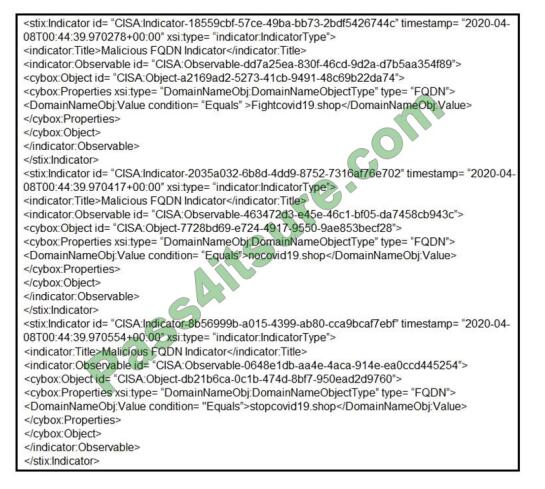
Refer to the exhibit. Which two actions should be taken based on the intelligence information? (Choose two.)
A. Block network access to all .shop domains
B. Add a SIEM rule to alert on connections to identified domains.
C. Use the DNS server to block hole all .shop requests.
D. Block network access to identified domains.
E. Route traffic from identified domains to block holes.
Correct Answer: BD
QUESTION 9
Which tool is used for reverse engineering malware?
A. Ghidra
B. SNORT
C. Wireshark
D. NMAP
Correct Answer: A
Reference: https://www.nsa.gov/resources/everyone/ghidra/#:~:text=Ghidra%20is%20a%20software%20reverse,in%20t
heir%20networks%20and%20systems.
QUESTION 10
An engineer received a report of a suspicious email from an employee. The employee had already opened the
attachment, which was an empty Word document. The engineer cannot identify any clear signs of compromise but while
reviewing running processes, observes that PowerShell.exe was spawned by cmd.exe with a grandparent winword.exe
process. What is the recommended action the engineer should take?
A. Upload the file signature to threat intelligence tools to determine if the file is malicious.
B. Monitor processes as this are the standard behavior of Word macro embedded documents.
C. Contain the threat for further analysis as this is an indication of suspicious activity.
D. Investigate the sender of the email and communicate with the employee to determine the motives.
Correct Answer: A
QUESTION 11
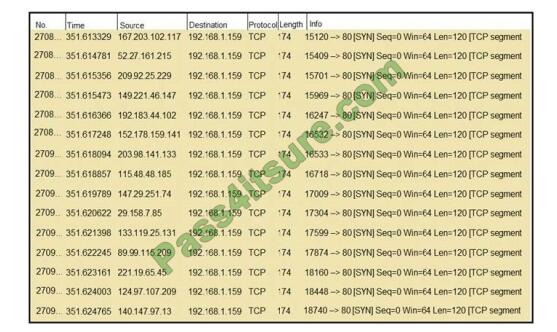
Refer to the exhibit. What should an engineer determine from this Wireshark capture of suspicious network traffic?
A. There are signs of SYN flood attack, and the engineer should increase the backlog and recycle the oldest half-open
TCP connections.
B. There are signs of a malformed packet attack, and the engineer should limit the packet size and set a threshold of
bytes as a countermeasure.
C. There are signs of a DNS attack, and the engineer should hide the BIND version and restrict zone transfers as a
countermeasure.
D. There are signs of ARP spoofing, and the engineer should use Static ARP entries and IP address-to-MAC address
mappings as a countermeasure.
Correct Answer: A
QUESTION 12
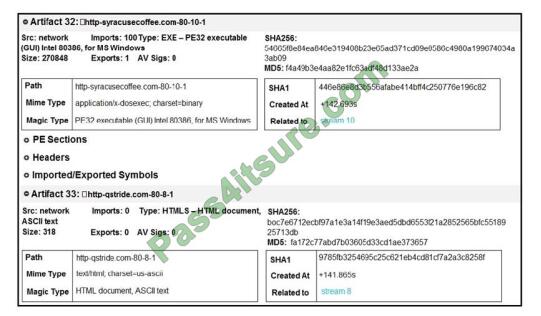
Refer to the exhibit. What do these artifacts indicate?
A. An executable file is requesting an application download.
B. A malicious file is redirecting users to different domains.
C. The MD5 of a file is identified as a virus and is being blocked.
D. A forged DNS request is forwarding users to malicious websites.
Correct Answer: A
QUESTION 13
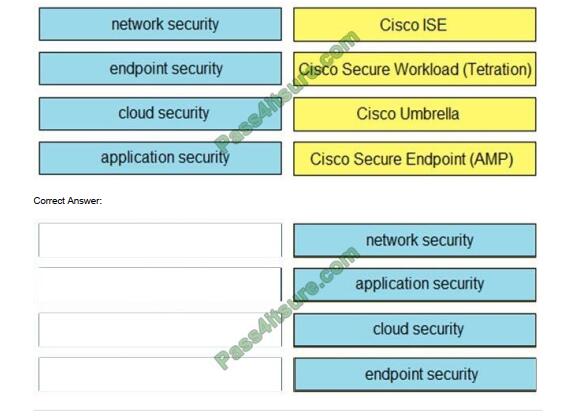
DRAG-DROP
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Select and Place:
QUESTION 14
Which information is provided bout the object file by the “-h” option in the objdump line command objdump ? oasys ? vax? fu.o?
A. bfdname
B. debugging
C. help
D. headers
Correct Answer: D
Reference: https://sourceware.org/binutils/docs/binutils/objdump.html
QUESTION 15
DRAG-DROP
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.

Finally
This blog Exampass shares some of the 300-215 exam questions, 300-215 PDFs from Pass4itSure. You can visit https://www.pass4itsure.com/300-215.html to get the complete Cisco 300-725 exam dumps questions (Total Q&As: 59). Trust Pass4itSure, has many years of experience. It’s all okay. Never give up!
PS.
Pass4itSure has started a special 15% discount on the Cisco code. Come and get 300-215 exam questions. You certainly don’t want to miss the proposal.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

