Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Valid Microsoft AZ-500 dumps questions shared by Pass4itsure for helping to pass the Microsoft AZ-500 exam! Get the newest Pass4itsure Microsoft AZ-500 exam dumps with VCE and PDF here: https://www.pass4itsure.com/az-500.html (242 Q&As Dumps).
Suitable for AZ-500 complete Microsoft learning pathway
The content is rich and diverse, and learning will not become boring. You can learn in multiple ways through the Microsoft AZ-500 exam.
- Download
- Watch the video
- Answer practice questions, the actual test
AZ-500 Microsoft Azure Security Technologies
Free Microsoft AZ-500 dumps download
[PDF] Free Microsoft AZ-500 dumps pdf download https://drive.google.com/file/d/188m4vbckiCAI20mbsqgn8o64Bi9XCO1u/view?usp=sharing
Pass4itsure offers the latest Microsoft AZ-500 practice test free of charge 1-13
QUESTION 1
You have an Azure subscription that contains the virtual networks shown in the following table.
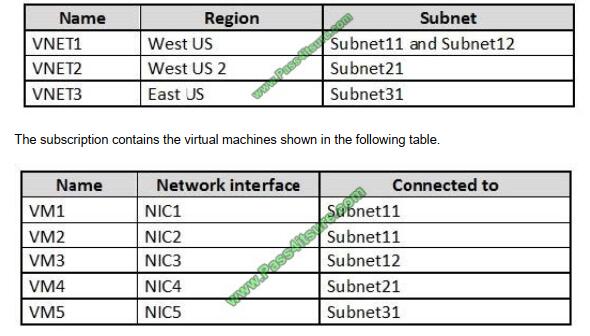
On NIC1, you configure an application security group named ASG1. On which other network interfaces can you
configure ASG1?
A. NIC2 only
B. NIC2, NIC3, NIC4, and NIC5
C. NIC2 and NIC3 only
D. NIC2, NIC3, and NIC4 only
Correct Answer: C
Only network interfaces in NVET1, which consists of Subnet11 and Subnet12, can be configured in ASG1, as all
network interfaces assigned to an application security group have to exist in the same virtual network that the first
network interface assigned to the application security group is in.
Reference: https://azure.microsoft.com/es-es/blog/applicationsecuritygroups/
QUESTION 2
From the Azure portal, you are configuring an Azure policy.
You plan to assign policies that use the DeployIfNotExist, AuditIfNotExist, Append, and Deny effects.
Which effect requires a managed identity for the assignment?
A. AuditIfNotExist
B. Append
C. DeployIfNotExist
D. Deny
Correct Answer: C
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity.
References: https://docs.microsoft.com/bs-latn-ba/azure/governance/policy/how-to/remediate-resources
QUESTION 3
You have an Azure subscription named Sub1 that contains the resources shown in the following table.
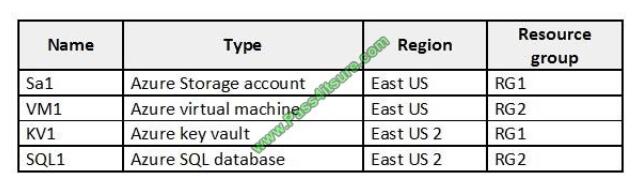
You need to ensure that you can provide VM1 with secure access to a database on SQL1 by using a contained
database user. What should you do?
A. Enable a managed service identity on VM1.
B. Create a secret in KV1.
C. Configure a service endpoint on SQL1.
D. Create a key in KV1.
Correct Answer: B
QUESTION 4
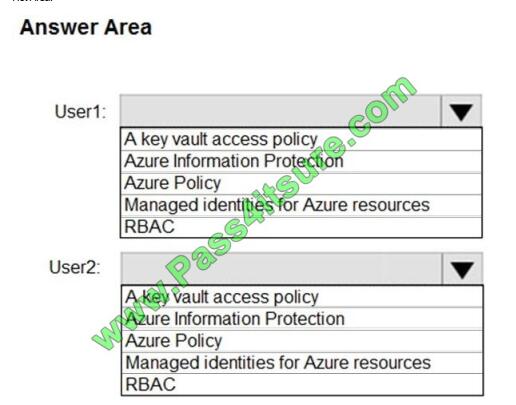
You have an Azure key vault.
You need to delegate administrative access to the key vault to meet the following requirements:
Provide a user named User1 with the ability to set advanced access policies for the key vault.
Provide a user named User2 with the ability to add and delete certificates in the key vault.
Use the principle of least privilege.
What should you use to assign access to each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
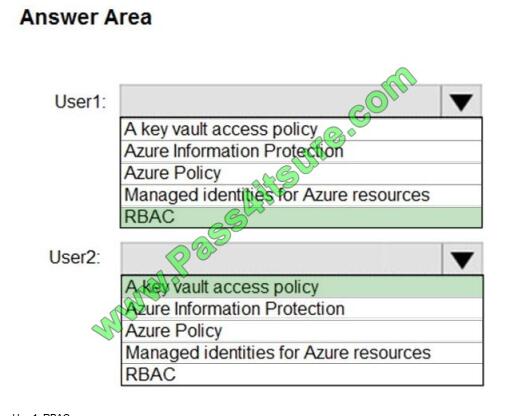
User1: RBAC
RBAC is used as the Key Vault access control mechanism for the management plane. It would allow a user with the
proper identity to:
set Key Vault access policies
create, read, update, and delete key vaults
set Key Vault tags
Note: Role-based access control (RBAC) is a system that provides fine-grained access management of Azure
resources. Using RBAC, you can segregate duties within your team and grant only the amount of access to users that
they need to
perform their jobs.
User2: A key vault access policy
A key vault access policy is the access control mechanism to get access to the key vault data plane. Key Vault access
policies grant permissions separately to keys, secrets, and certificates.
References: https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
QUESTION 5
You need to ensure that User2 can implement PIM. What should you do first?
A. Assign User2 the Global administrator role.
B. Configure authentication methods for contoso.com.
C. Configure the identity secure score for contoso.com.
D. Enable multi-factor authentication (MFA) for User2.
Correct Answer: A
To start using PIM in your directory, you must first enable PIM.
1. Sign in to the Azure portal as a Global Administrator of your directory.
You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft
account (for example, @outlook.com), to enable PIM for a directory.
Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-getting-started
QUESTION 6
Your company plans to create separate subscriptions for each department. Each subscription will be associated with the
same Azure Active Directory (Azure AD) tenant.
You need to configure each subscription to have the same role assignments. What should you use?
A. Azure Security Center
B. Azure Policy
C. Azure AD Privileged Identity Management (PIM)
D. Azure Blueprints
Correct Answer: D
Just as a blueprint allows an engineer or an architect to sketch a project\\’s design parameters, Azure Blueprints
enables cloud architects and central information technology groups to define a repeatable set of Azure resources that
implements and adheres to an organization\\’s standards, patterns, and requirements.
Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such
as: Role Assignments Policy Assignments Azure Resource Manager templates Resource Groups
Reference: https://docs.microsoft.com/en-us/azure/governance/blueprints/overview
QUESTION 7
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have an Azure Subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or
Windows Server 2016.
You need to deploy Microsoft Antimalware to the virtual machines.
Solution: You add an extension to each virtual machine.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
You can use Visual Studio to enable and configure the Microsoft Antimalware service. This entails selecting Microsoft
Antimalware extension from the dropdown list under Installed Extensions and click Add to configure with default
antimalware configuration.
References: https://docs.microsoft.com/en-us/azure/security/fundamentals/antimalware
QUESTION 8
You have an Azure subscription named Sub1. Sub1 contains a virtual network named VNet1 that contains one subnet
named Subnet1.
Subnet1 contains an Azure virtual machine named VM1 that runs Ubuntu Server 18.04.
You create a service endpoint for MicrosoftStorage in Subnet1.
You need to ensure that when you deploy Docker containers to VM1, the containers can access Azure Storage
resources by using the service endpoint.
What should you do on VM1 before you deploy the container?
A. Create an application security group and a network security group (NSG).
B. Edit the docker-compose.yml file.
C. Install the container network interface (CNI) plug-in.
Correct Answer: C
The Azure Virtual Network container network interface (CNI) plug-in installs in an Azure Virtual Machine. The plug-in
supports both Linux and Windows platform. The plug-in assigns IP addresses from a virtual network to containers
brought
up in the virtual machine, attaching them to the virtual network, and connecting them directly to other containers and
virtual network resources. The plug-in doesn\\’t rely on overlay networks, or routes, for connectivity, and provides the
same
performance as virtual machines.
The following picture shows how the plug-in provides Azure Virtual Network capabilities to Pods:
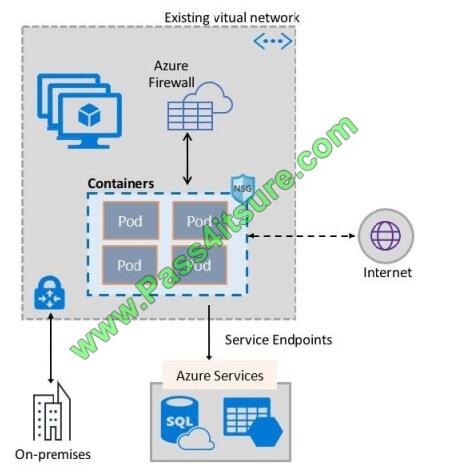
References: https://docs.microsoft.com/en-us/azure/virtual-network/container-networking-overview
QUESTION 9
You create resources in an Azure subscription as shown in the following table.
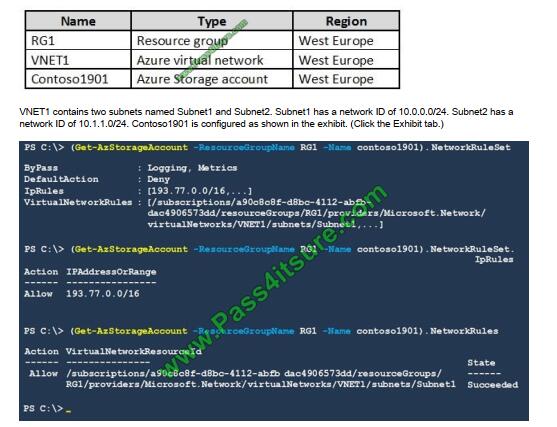
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct
selection is worth one point.
Hot Area:

Box 1: Yes
Access from Subnet1 is allowed.
Box 2: No
No access from Subnet2 is allowed.
Box 3: Yes
Access from IP address 193.77.10.2 is allowed.
QUESTION 10
You have 15 Azure virtual machines in a resource group named RG1.
All virtual machines run identical applications.
You need to prevent unauthorized applications and malware from running on the virtual machines.
What should you do?
A. Apply an Azure policy to RG1.
B. From Azure Security Center, configure adaptive application controls.
C. Configure Azure Active Directory (Azure AD) Identity Protection.
D. Apply a resource lock to RG1.
Correct Answer: B
Adaptive application control is an intelligent, automated end-to-end application whitelisting solution from Azure Security
Center. It helps you control which applications can run on your Azure and non-Azure VMs (Windows and Linux), which,
among other benefits, helps harden your VMs against malware. Security Center uses machine learning to analyze the
applications running on your VMs and helps you apply the specific whitelisting rules using this intelligence.
Reference: https://docs.microsoft.com/en-us/azure/security-center/security-center-adaptive-application
QUESTION 11
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzureRmNetworkSecurityRuleConfig and receive the output shown in the following exhibit.
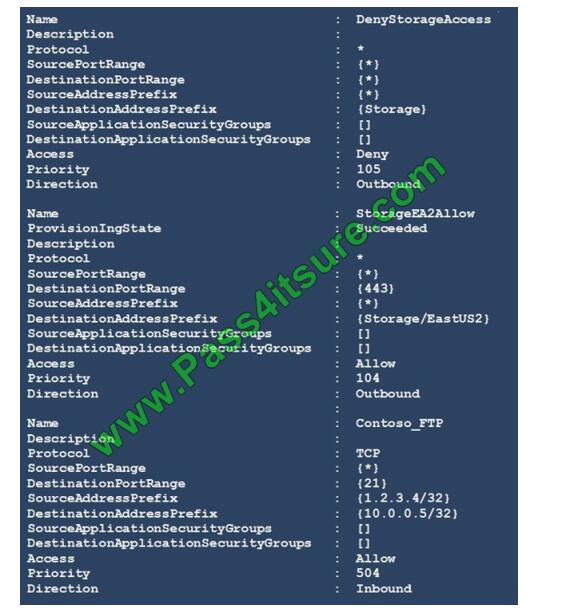
Use the drop-down menus to select the answer choice that completes each statement based on the information
presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:

Box 1: able to connect to East US 2
The StorageEA2Allow has DestinationAddressPrefix {Storage/EastUS2}
Box 2: allowed
TCP Port 21 controls the FTP session. Contoso_FTP has SourceAddressPrefix {1.2.3.4/32} and
DestinationAddressPrefix {10.0.0.5/32}
Note:
The Get-AzureRmNetworkSecurityRuleConfig cmdlet gets a network security rule configuration for an Azure network
security group. Security rules in network security groups enable you to filter the type of network traffic that can flow in
and
out of virtual network subnets and network interfaces.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/manage-network-security-group
QUESTION 12
You are evaluating the effect of the application security groups on the network communication between the virtual
machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
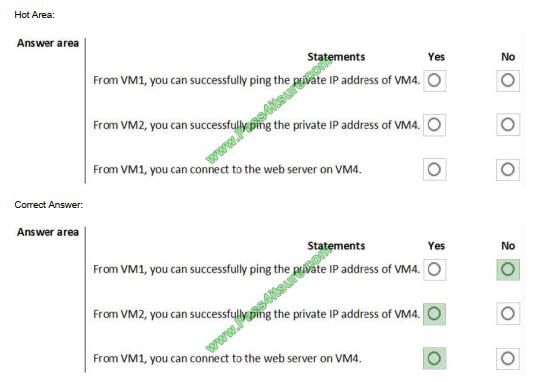
Box 1: No. VM4 is in Subnet13 which has NSG3 attached to it.
VM1 is in ASG1. NSG3 would only allow ICMP pings from ASG2 but not ASG1. Only TCP traffic is allowed from ASG1.
NSG3 has the inbound security rules shown in the following table.
Box 2: Yes.
VM2 is in ASG2. Any protocol is allowed from ASG2 so ICMP ping would be allowed.
Box3. VM1 is in ASG1. TCP traffic is allowed from ASG1 so VM1 could connect to the web server as connections to the
web server would be on ports TCP 80 or TCP 443.
QUESTION 13
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named
contoso.com.
You are assigned the Global administrator role for the tenant. You are responsible for managing Azure Security Center
settings.
You need to create a custom sensitivity label.
What should you do?
A. Create a custom sensitive information type.
B. Elevate access for global administrators in Azure AD.
C. Change Azure Security Center to use Standard-tier-pricing.
D. Enable integration with Microsoft Cloud App Security.
Correct Answer: A
First, you need to create a new sensitive information type because you can\\’t directly modify the default rules.
References: https://docs.microsoft.com/en-us/office365/securitycompliance/customize-a-built-in-sensitive-informationtype
What customers say about Pass4itsure
Latest Microsoft dumps discount code “Microsoft” – Pass4itsure

Summarize:
[Q1-Q13] Free Microsoft AZ-500 dumps pdf download https://drive.google.com/file/d/188m4vbckiCAI20mbsqgn8o64Bi9XCO1u/view?usp=sharing
Share all the resources: Latest Microsoft AZ-500 practice questions, latest Microsoft AZ-500 pdf dumps, Microsoft AZ-500 exam video learning. Latest updated Microsoft AZ-500 dumps https://www.pass4itsure.com/az-500.html Study hard and practices a lot. This will help you prepare for the AZ-500 exam. Good luck!
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

