Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Pass4itsure share these resources with you. Both VCE and PDF dumps contain the latest CompTIA SY0-501 exam questions, which will ensure your SY0-501 exam 100% passed! You can get SY0-501 VCE dumps and SY0-501 PDF dumps from Pass4itsure. Please get the latest Pass4itsure SY0-501 dumps here: https://www.pass4itsure.com/sy0-501.html (1139 QA Dumps).
Learn to grow, not just pass CompTIA SY0-501 exam
This is why Pass4itsure provides you with real and proven SY0-501 exam preparation materials, which will help you broaden your thinking.

Taking the Pass4itsure SY0-501 latest exam will help you easily prepare and pass the SY0-501 exam. In addition, you can also obtain the following advantages in the SY0-501 exam training materials.
- SY0-501 pdf dumps and practice test
- Comprehensive coverage of SY0-501 exam syllabus
- Update SY0-501 exam braindumps
CompTIA SY0-501 pdf dumps free
[free pdf] CompTIA SY0-501 pdf dumps update 2020 https://drive.google.com/file/d/18OyZiENtTfSD7z9Uyi9ZY5WWSe4vGKQ0/view?usp=sharing
CompTIA Security+ SY0-501 dumps practice test(questions & answers)
QUESTION 1
An organization is looking to build its second head office another city, which has a history flooding with an average of
two flooding every 100 years. The estimated building cost is $1 million, an the estimated damage due to flooding is half
of the building\\’s cost.
Given this information, which of the following is the SLE?
A. $50,000
B. $250,000
C. $500,000
D. $1,000,000
Correct Answer: C
QUESTION 2
Which of the following is a deployment concept that can be used to ensure only the required OS access is exposed to
software applications?
A. Staging environment
B. Sandboxing
C. Secure baseline
D. Trusted OS
Correct Answer: B
QUESTION 3
An attacker captures the encrypted communication between two parties for a week, but is unable to decrypt the
messages. The attacker then compromises the session key during one exchange and successfully compromises a
single message. The attacker plans to use this key to decrypt previously captured and future communications, but is
unable to. This is because the encryption scheme in use adheres to:
A. Asymmetric encryption
B. Out-of-band key exchange
C. Perfect forward secrecy
D. Secure key escrow
Correct Answer: C
QUESTION 4
Which of the following explains why vendors publish MD5 values when they provide software patches for their
customers to download over the Internet?
A. The recipient can verify integrity of the software patch.
B. The recipient can verify the authenticity of the site used to download the patch.
C. The recipient can request future updates to the software using the published MD5 value.
D. The recipient can successfully activate the new software patch.
Correct Answer: A
QUESTION 5
A company recently implemented a new security system. In the course of configuration, the security administrator adds
the following entry:
#Whitelist USB\VID_13FEandPID_4127andREV_0100
Which of the following security technologies is MOST likely being configured?
A. Application whitelisting
B. HIDS
C. Data execution prevention
D. Removable media control
Correct Answer: D
QUESTION 6
In terms of encrypting data, which of the following is BEST described as a way to safeguard password data by adding
random data to it in storage?
A. Using salt
B. Using hash algorithms
C. Implementing elliptical curve
D. Implementing PKI
Correct Answer: A
QUESTION 7
An organization wants to set up a wireless network in the most secure way. Budget is not a major consideration, and the
organization is willing to accept some complexity when clients are connecting. It is also willing to deny wireless
connectivity for clients who cannot be connected in the most secure manner. Which of the following would be the MOST
secure setup that conforms to the organization\\’s requirements?
A. Enable WPA2-PSK for older clients and WPA2-Enterprise for all other clients.
B. Enable WPA2-PSK, disable all other modes, and implement MAC filtering along with port security.
C. Use WPA2-Enterprise with RADIUS and disable pre-shared keys.
D. Use WPA2-PSK with a 24-character complex password and change the password monthly.
Correct Answer: C
QUESTION 8
A Chief Information Officer (CIO) has decided it is not cost effective to implement safeguards against a known
vulnerability. Which of the following risk responses does this BEST describe?
A. Transference
B. Avoidance
C. Mitigation
D. Acceptance
Correct Answer: D
QUESTION 9
A datacenter recently experienced a breach. When access was gained, an RF device was used to access an air-gapped
and locked server rack. Which of the following would BEST prevent this type of attack?
A. Faraday cage
B. Smart cards
C. Infrared detection
D. Alarms
Correct Answer: A
QUESTION 10
A security administrator needs to address the following audit recommendations for a public-facing SFTP server:
Users should be restricted to upload and download files to their own home directories only. Users should not be allowed
to use interactive shell login. Which of the following configuration parameters should be implemented? (Select TWO).
A. PermitTunnel
B. ChrootDirectory
C. PermitTTY
D. AllowTcpForwarding
E. IgnoreRhosts
Correct Answer: BC
QUESTION 11
Following the successful response to a data-leakage incident, the incident team lead facilitates an exercise that focuses
on continuous improvement of the organization\\’s incident response capabilities. Which of the following activities has
the incident team lead executed?
A. Lessons learned review
B. Root cause analysis
C. Incident audit
D. Corrective action exercise
Correct Answer: A
QUESTION 12
A systems administrator is attempting to recover from a catastrophic failure in the datacenter. To recover the domain
controller, the systems administrator needs to provide the domain administrator credentials. Which of the following
account types is the systems administrator using?
A. Local account
B. Guest account
C. Service account
D. User account
Correct Answer: C
QUESTION 13
Determine the types of attacks below by selecting an option from the dropdown list. Determine the types of Attacks from
right to a specific action.
Select and Place:
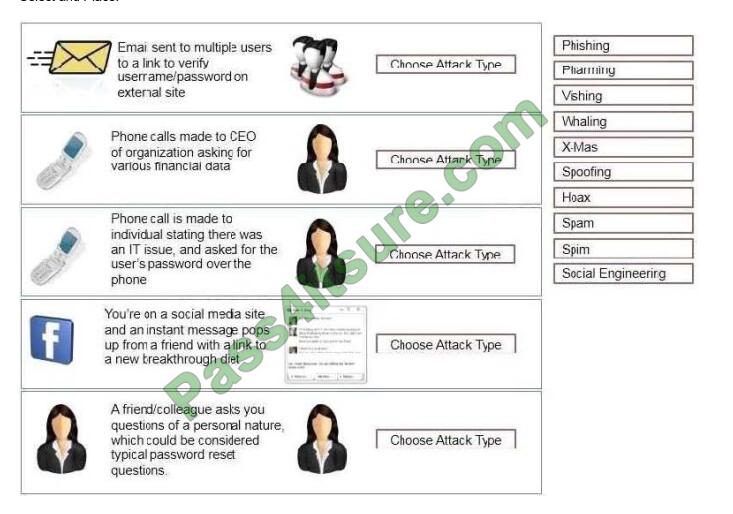
Correct Answer:
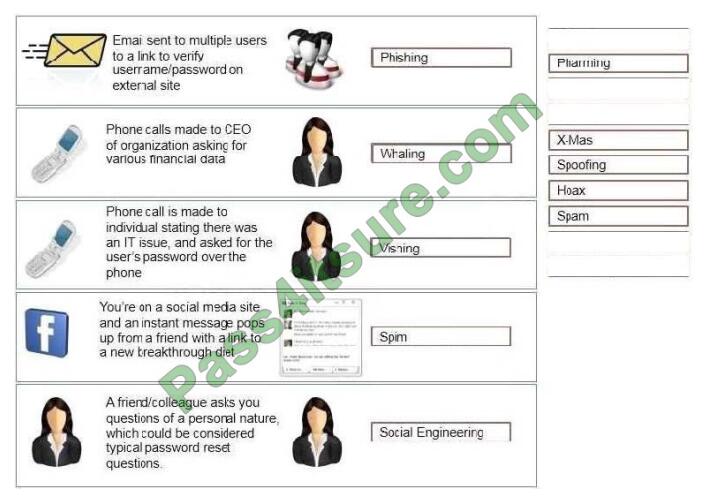
A. Phishing.
B. Whaling.
C. Vishing.
D. Spim.
E. Social engineering.
A: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an
attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a
password, credit card, social security, or bank account numbers, that the legitimate organization already has. The
website,
however, is bogus and set up only to steal the information the user enters on the page.
B: Whaling is a specific kind of malicious hacking within the more general category of phishing, which involves hunting
for data that can be used by the hacker. In general, phishing efforts are focused on collecting personal data about users.
In
whaling, the targets are high-ranking bankers, executives or others in powerful positions or job titles.
Hackers who engage in whaling often describe these efforts as “reeling in a big fish,” applying a familiar metaphor to the process of scouring technologies for loopholes and opportunities for data theft. Those who are engaged in whaling
may,
for example, hack into specific networks where these powerful individuals work or store sensitive data. They may also
set up keylogging or other malware on a work station associated with one of these executives. There are many ways
that
hackers can pursue whaling, leading C-level or top-level executives in business and government to stay vigilant about
the possibility of cyber threats.
C: Vishing is the act of using the telephone in an attempt to scam the user into surrendering private information that will
be used for identity theft. The scammer usually pretends to be a legitimate business, and fools the victim into thinking
he
or she will profit.
D: SPIM is a term sometimes used to refer to spam over IM (Instant Messaging). It\\’s also called just spam, instant
spam, or IM marketing. No matter what the name, it consists of unwanted messages transmitted through some form of
instant
messaging service, which can include Short Message Service (SMS).
E: Social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and
often involves tricking people into breaking normal security procedures. It is one of the greatest threats that
organizations
today encounter.
A social engineer runs what used to be called a “con game.” For example, a person using social engineering to break
into a computer network might try to gain the confidence of an authorized user and get them to reveal information that
compromises the network\\’s security. Social engineers often rely on the natural helpfulness of people as well as on their
weaknesses. They might, for example, call the authorized employee with some kind of urgent problem that requires
immediate network access. Appealing to vanity, appealing to authority, appealing to greed, and old-fashioned
eavesdropping are other typical social engineering techniques.
References:
http://www.webopedia.com/TERM/P/phishing.html
http://www.techopedia.com/definition/28643/whaling
http://www.webopedia.com/TERM/V/vishing.html
http://searchsecurity.techtarget.com/definition/social-engineering
The most important thing right now is practice, practice, and practice. The more you practice, the more you’ll get familiar with the CompTIA SY0-501 exam.
Following are some great features of Pass4itsure SY0-501 study material:

Pass4itsure discount code 2020
Up-To 12% discount on SY0-501 pdf dumps.

P.S.
This makes https://www.pass4itsure.com/sy0-501.html your sole companion in SY0-501 exam preparation. In this article, share the latest SY0-501 practice questions, SY0-501 pdf dump, and SY0-501 exam video learning. Study hard and practice a lot. This will help you prepare for the SY0-501 exam. good luck! (After completion, you may want to take a look at the other CompTIA exam! :))
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

