Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Valid Cisco 350-201 questions shared by Pass4itsure for helping to pass the Cisco 350-201 exam! Get the newest Pass4itsure Cisco 350-201 exam dumps with VCE and PDF here: https://www.pass4itsure.com/350-201.html (102 Q&As Dumps).
[Free PDF] Cisco 350-201 pdf Q&As https://drive.google.com/file/d/1WhCl7p_7kwA1vNkcZV1FJXM6gjy0ObLp/view?usp=sharing
Suitable for 350-201 complete Cisco learning pathway
The content is rich and diverse, and learning will not become boring. You can learn in multiple ways through the Cisco 350-201 exam.
- Download
- Answer practice questions, the actual Cisco 350-201 test
Cisco 350-201 Performing CyberOps Using Cisco Security Technologies (CBRCOR)
Free Cisco 350-201 dumps download
[PDF] Free Cisco 350-201 dumps pdf download https://drive.google.com/file/d/1WhCl7p_7kwA1vNkcZV1FJXM6gjy0ObLp/view?usp=sharing
Pass4itsure offers the latest Cisco 350-201 practice test free of charge 1-13
QUESTION 1
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their
organization monitors. The email includes a suspicious attachment titled “Invoice RE: 0004489”. The hash of the file is
gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this
hash is found anywhere on the web.
What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
Correct Answer: D
QUESTION 2
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased
customer demands, the company recently started to accept credit card payments and acquired a POS terminal. Which
compliance regulations must the audit apply to the company?
A. HIPAA
B. FISMA
C. COBIT
D. PCI DSS
Correct Answer: D
Reference: https://upserve.com/restaurant-insider/restaurant-pos-pci-compliance-checklist/
QUESTION 3
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having
the names of the 3 destination countries and the user\\’s working hours, what must the analyst do next to detect an
abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
Correct Answer: D
QUESTION 4
Refer to the exhibit. A security analyst needs to investigate a security incident involving several suspicious connections
with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?
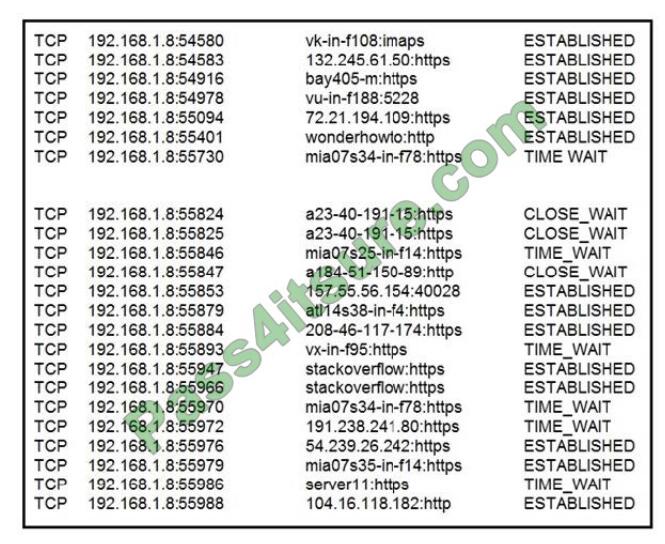
A. packet sniffer
B. malware analysis
C. SIEM
D. firewall manager
Correct Answer: A
QUESTION 5

Refer to the exhibit. Which data format is being used?
A. JSON
B. HTML
C. XML
D. CSV
Correct Answer: B
QUESTION 6
An engineer is moving data from NAS servers in different departments to a combined storage database so that the data
can be accessed and analyzed by the organization on-demand. Which data management process is being used?
A. data clustering
B. data regression
C. data ingestion
D. data obfuscation
Correct Answer: A
QUESTION 7
Refer to the exhibit. An employee is a victim of a social engineering phone call and installs remote access software to
allow an “MS Support” technician to check his machine for malware. The employee becomes suspicious after the
remote technician requests payment in the form of gift cards. The employee has copies of multiple, unencrypted
database files, over 400 MB each, on his system and is worried that the scammer copied the files off but has no proof of
it. The remote technician was connected sometime between 2:00 pm and 3:00 pm over https.
What should be determined regarding data loss between the employee\\’s laptop and the remote technician\\’s system?
A. No database files were disclosed
B. The database files were disclosed
C. The database files integrity was violated
D. The database files were intentionally corrupted, and encryption is possible
Correct Answer: C
QUESTION 8
How does Wireshark decrypt TLS network traffic?
A. with a key log file using per-session secrets
B. using an RSA public key
C. by observing DH key exchange
D. by defining a user-specified decode-as
Correct Answer: A
Reference: https://wiki.wireshark.org/TLS
QUESTION 9
An organization had a breach due to a phishing attack. An engineer leads a team through the recovery phase of the
incident response process. Which action should be taken during this phase?
A. Host a discovery meeting and define configuration and policy updates
B. Update the IDS/IPS signatures and reimage the affected hosts
C. Identify the systems that have been affected and tools used to detect the attack
D. Identify the traffic with data capture using Wireshark and review email filters
Correct Answer: C
QUESTION 10
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the
files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the
network usage and discovers that it is abnormally high.
Which step should be taken to continue the investigation?
A. Run the sudo sysdiagnose command
B. Run the sh command
C. Run the w command
D. Run the who command
Correct Answer: A
Reference: https://eclecticlight.co/2016/02/06/the-ultimate-diagnostic-tool-sysdiagnose/
QUESTION 11
DRAG DROP
An organization lost connectivity to critical servers, and users cannot access business applications and internal
websites. An engineer checks the network devices to investigate the outage and determines that all devices are
functioning. Drag and drop the steps from the left into the sequence on the right to continue investigating this issue. Not
all options are used.
Select and Place:
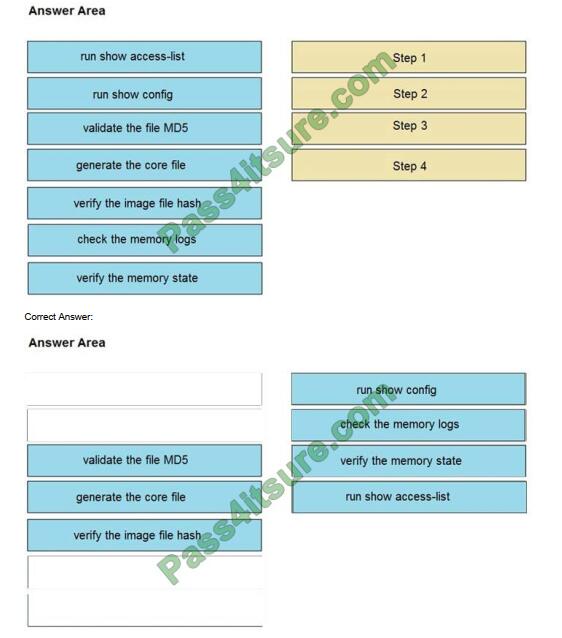
QUESTION 12
A company\\’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not
deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An
analyst conducted the risk assessment using the threat sources, events, and vulnerabilities.
Which additional element is needed to calculate the risk?
A. assessment scope
B. event severity and likelihood
C. incident response playbook
D. risk model framework
Correct Answer: D
QUESTION 13
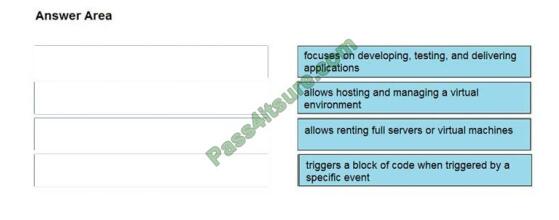
DRAG DROP
Drag and drop the cloud computing service descriptions from the left onto the cloud service categories on the right.
Select and Place:
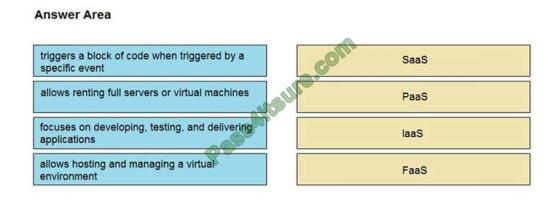
Correct Answer:
Pass4itsure Cisco exam dumps discount code share

Summarize:
[Q1-Q13] Free Cisco 350-201 pdf download https://drive.google.com/file/d/1WhCl7p_7kwA1vNkcZV1FJXM6gjy0ObLp/view?usp=sharing
Share all the resources: Latest Cisco 350-201 practice questions, latest Cisco 350-201 pdf dumps. The latest updated Cisco 350-201 dumps https://www.pass4itsure.com/350-201.html Study hard and practices a lot. This will help you prepare for the Cisco 350-201 exam. Good luck!
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

