Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
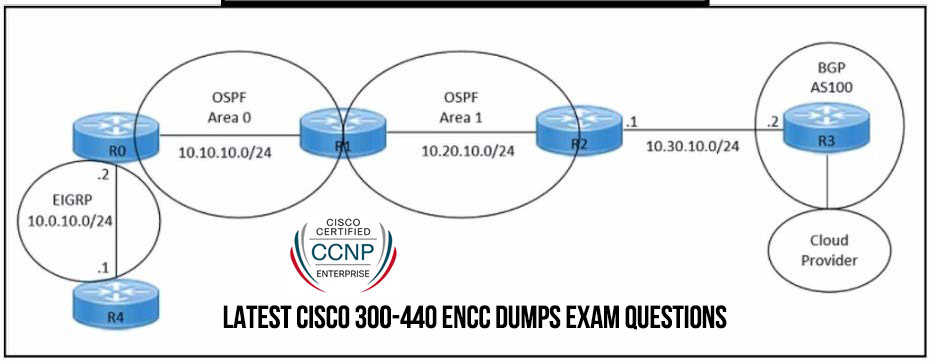
Cisco 300-440 ENCC dumps are the exam materials that will help you pass the 300-440 ENCC certification exam successfully. They are the latest on the Internet! Download Cisco 300-440 ENCC dumps: https://www.leads4pass.com/300-440.html, which contains 38 latest exam questions and answers to ensure you pass the exam successfully on your first attempt.
Welcome to take the Cisco 300-440 online practice test
| Number of exam questions | Verify answer |
| 15 | Check |
Question 1:
A cloud engineer is setting up a new set of nodes in the AWS EKS cluster to manage database integration with Mongo Atlas. The engineer set up security to Mongo but now wants to ensure that the nodes are also secure on the network side. Which feature in AWS should the engineer use?
A. EC2 Trust Lock
B. security groups
C. tagging
D. key pairs
Security groups are a feature in AWS that allow you to control the inbound and outbound traffic to your instances. They act as a virtual firewall that can filter the traffic based on the source, destination, protocol, and port. You can assign one or more security groups to your instances, and each security group can have multiple rules. Security groups are stateful, meaning that they automatically allow the response traffic for any allowed inbound traffic, and vice versa. Security groups are essential for securing your nodes in the AWS EKS cluster, as they can prevent unauthorized access to your Mongo Atlas database or other resources.
References: AWS Security Groups Security Groups for Your VPC Security Groups for Your Amazon EC2 Instances Security Groups for Your Amazon EKS Cluster
Question 2:
An engineer must enable the OMP advertisement of BGP routes for a specific VRF instance on a Cisco IOS XE SD-WAN device. What should be configured after the global address-family ipv4 is configured?
A. Set the VRF-specific route advertisements.
B. Enable bgp advertisement.
C. Enter sdwan mode.
D. Disable bgp advertisement.
To enable the OMP advertisement of BGP routes for a specific VRF instance on a Cisco IOS XE SD-WAN device, the engineer must first configure the global address-family ipv4 and then enable bgp advertisement under the vrf definition.
This will allow the device to advertise the BGP routes learned from the cloud provider to the OMP control plane, which will then distribute them to the other SD-WAN devices in the overlay network.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0, Module 3:Implementing Cloud Connectivity, Lesson 3: Configuring IPsec VPN from Cisco IOS XE to AWS, Topic: Configuring BGP on the Cisco IOS XE Device, Page 3-24.
Question 3:
Which approach does a centralized internet gateway use to provide connectivity to SaaS applications?
A. A cloud-based proxy server routes traffic from the on-premises infrastructure to the SaaS provider data center.
B. Internet traffic from the on-premises infrastructure is routed through a centralized gateway that provides access controls for SaaS applications.
C. VPN connections are used to provide secure access to SaaS applications from the on- premises infrastructure.
D. A dedicated, private connection is established between the on-premises infrastructure and the SaaS provider data center using colocation services.
A centralized internet gateway is a network design that routes all internet- bound traffic from the on-premises infrastructure through a single point of egress, typically located at the data center or a regional hub1. This approach allows the enterprise to apply consistent security policies and access controls for SaaS applications, as well as optimize the bandwidth utilization and performance of the WAN links. A centralized internet gateway can use various technologies to provide connectivity to SaaS applications, such as proxy servers, firewalls, web filters, and WAN optimizers. However, a cloud-based proxy server (option A) is not a part of the centralized internet gateway, but rather a separate service that can be used to route traffic from the on-premises infrastructure to the SaaS provider data center4. VPN connections (option C) and dedicated, private connections (option D) are also not related to the centralized internet gateway, but rather alternative ways of providing secure and reliable access to SaaS applications from the on- premises infrastructure5. Therefore, the correct answer is option B, which describes the basic function of a centralized internet gateway.
Question 4:
Which method is used to create authorization boundary diagrams (ABDs)?
A. identify only interconnected systems that are FedRAMP-authorized
B. show all networks in CIDR notation only
C. identify all tools as either external or internal to the boundary
D. show only minor or small upgrade level software components
According to the FedRAMP Authorization Boundary Guidance document, the method used to create authorization boundary diagrams (ABDs) is to identify all tools as either external orinternal to the boundary. The ABD is a visual representation of the components that make up the authorization boundary, which includes all technologies, external and internal services, and leveraged systems and accounts for all federal information, data, and metadata that a Cloud Service Offering (CSO) is responsible for. The ABD should illustrate a CSP\’s scope of control over the system and show components or services that are leveraged from external services or controlled by the customer. The other options are incorrect because they do not capture the full scope and details of the authorization boundary as required by FedRAMP.
References: FedRAMP Authorization Boundary Guidance document
Question 5:
Refer to the exhibit.

While troubleshooting an IPsec connection between a Cisco WAN edge router and an Amazon Web Services (AWS) endpoint, a network engineer observes that the security association status is active, but no traffic flows between the devices What is the problem?
A. wrong ISAKMP policy
B. identity mismatch
C. wrong encryption
D. IKE version mismatch
An identity mismatch occurs when the local and remote identities configured on the IPsec peers do not match. This can prevent the establishment of an IPsec tunnel or cause traffic to be dropped by the IPsec policy. In this case, the network
engineer should verify that the local and remote identities configured on the Cisco WAN edge router and the AWS endpoint match the values expected by each peer. The identities can be an IP address, a fully qualified domain name (FQDN),
or a distinguished name (DN). The identities are exchanged during the IKE phase 1 negotiation and are used to authenticate the peers. If the identities do not match, the peers will reject the IKE proposal and the IPsec tunnel will not be
established or will be torn down.
References: Configure IOS-XE Site-to-Site VPN Connection to Amazon Web Services, Topic:Troubleshooting
Designing and Implementing Cloud Connectivity (ENCC) v1.0, Module 3:
Implementing Cloud Connectivity, Lesson 2: Implementing Cisco SD-WAN Cloud OnRamp for IaaS, Topic: Troubleshooting Cisco SD-WAN Cloud OnRamp for IaaS Cisco IOS Security Configuration Guide, Release 15MandT, Chapter:
Configuring IPsec Network Security, Topic: Configuring IPsec Identity and Peer Addressing
Question 6:
Refer to the exhibits.
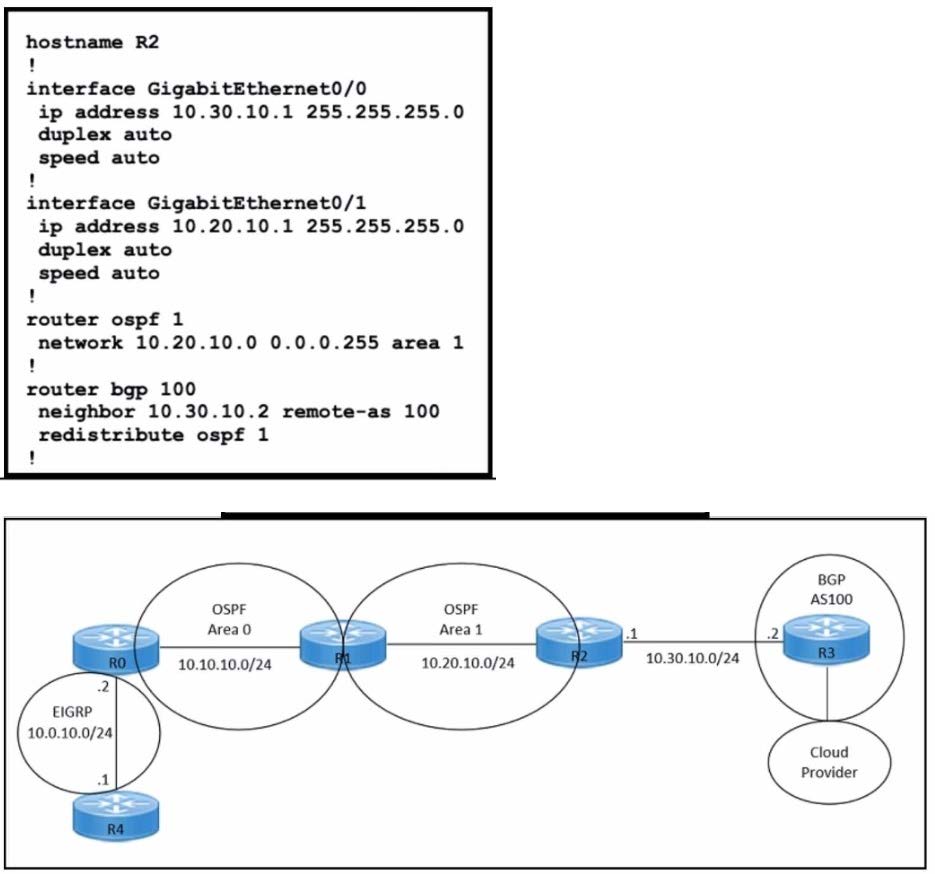
An engineer must redistribute only the 10.0.10.0/24 network into BGP to connect an on-premises network to a public cloud provider. These routes are currently redistributed:
Which command is missing on router R2?
A. neighbor 10.0.10.2 remote-as 100
B. redistribute ospf 1 match internal
C. redistribute ospf 1 match external
D. neighbor 10.0.10.0/24 remote-as 100
The command redistribute ospf 1 match external is missing on router R2. This command is needed to redistribute only the external OSPF routes into BGP. The external OSPF routes are those that are learned from another routing protocol or
redistributed into OSPF. In this case, the 10.0.10.0/24 network is an external OSPF route, as it is redistributed from EIGRP into OSPF on router R1. The other commands are either already present or not relevant for this scenario.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0, Module 3:
Implementing Cloud Connectivity, Lesson 3.1: Implementing IPsec VPN from Cisco IOS XE to AWS, Topic 3.1.2: Configure BGP on the Cisco IOS XE Router Security for VPNs with IPsec Configuration Guide, Cisco IOS XE, Chapter:
Configuring IPsec VPNs with Dynamic Routing Protocols, Section: Configuring BGP over IPsec VPNs
Question 7:
DRAG DROP
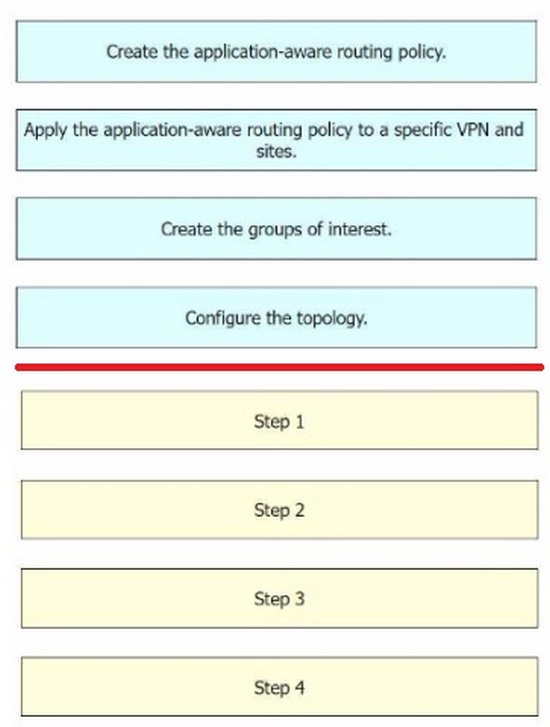
An engineer must use Cisco vManage to configure an application-aware routing policy Drag and drop the steps from the left onto the order on the right to complete the configuration.
Select and Place:
Correct Answer:
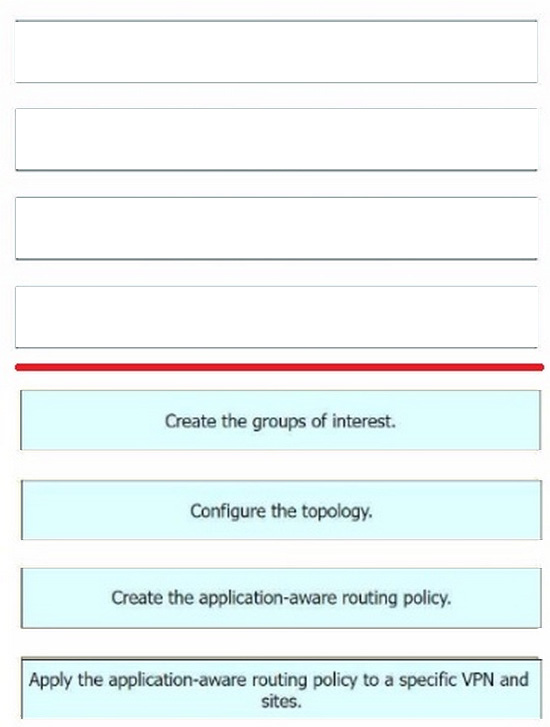
Step 1 = Create the groups of interest.
Step 2 = Configure the topology.
Step 3 = Create the application-aware routing policy.
Step 4 = Apply the application-aware routing policy to a specific VPN and sites.
The process of configuring an application-aware routing policy in Cisco vManage involves several steps.
Create the groups of interest: This is the first step where you define the applications or groups that the policy will affect. Configure the topology: This involves setting up the network topology that the policy will operate within.
Create the application-aware routing policy: After setting up the groups and topology, you then create the application-aware routing policy. This policy tracks network and path characteristics of the data plane tunnels between Cisco SD- WAN
devices and uses the collected information to compute optimal paths for data traffic.
Apply the application-aware routing policy to a specific VPN and sites: Finally, the created policy is applied to a specific VPN and sites. This allows the policy to affect the desired network traffic.
References:
Designing and Implementing Cloud Connectivity (ENCC) v1.0 Learning Plan: Designing and Implementing Cloud Connectivity v1.0 (ENCC 300- 440)
Information About Application-Aware Routing – Cisco Configuring Application-Aware Routing (AAR) Policies | NetworkAcademy.io Policies Configuration Guide, Cisco IOS XE SD-WAN Releases 16.11, 16.12
Question 8:
Which architecture model establishes internet-based connectivity between on-premises networks and AWS cloud resources?
A. That establishes an iPsec VPN tunnel with Internet Key Exchange (IKE) for secure key negotiation and encrypted data transmission
B. That relies on AWS Elastic Load Balancing (ELB) for traffic distribution and uses SSL/TLS encryption for secure data transmission.
C. That employs AWS Direct Connect for a dedicated network connection and uses private IP addresses tor secure communication.
D. That uses Amazon CloudFrontfor caching and distributing content globally and uses HTTPS for secure data transfer.
The architecture model that establishes internet-based connectivity between on-premises networks and AWS cloud resources is the one that establishes an iPsec VPN tunnel with Internet Key Exchange (IKE) for secure key negotiation and encrypted data transmission. This model is also known as the VPN CloudHub model. It allows multiple remote sites to connect to the same virtual private gateway in AWS, creating a hub-and- spoke topology. The VPN CloudHub model provides the following benefits: It enables secure communication between remote sites and AWS over the public internet, using encryption and authentication protocols such as IPsec and IKE. It supports dynamic routing protocols such as BGP, which can automatically adjust the routing tables based on the availability and performance of the VPN tunnels. It allows for redundancy and load balancing across multiple VPN tunnels, increasing the reliability and throughput of the connectivity. It simplifies the management and configuration of the VPN connections, as each remote site only needs to establish one VPN tunnel to the virtual private gateway in AWS, rather than multiple tunnels to different VPCs or regions. The other options are not correct because they do not establish internet-based connectivity between on-premises networks and AWS cloud resources. Option B relies on AWS Elastic Load Balancing (ELB) for traffic distribution and uses SSL/TLS encryption for secure data transmission. However, ELB is a service that distributes incoming traffic across multiple targets within a VPC, not across different networks. Option C employs AWS Direct Connect for a dedicated network connection and uses private IP addresses for secure communication. However, AWS Direct Connect is a service that establishes a private connection between on-premises networks and AWS, bypassing the public internet. Option D uses Amazon CloudFront for caching and distributing content globally and uses HTTPS for secure data transfer. However, Amazon CloudFront is a service that delivers static and dynamic web content to end users, not to on-premises networks.
References:
1: Designing and Implementing Cloud Connectivity (ENCC, Track 1 of 5)
2: Cisco ASA Site-to-Site VPN
3: What Is Elastic Load Balancing?
4: What is AWS Direct Connect?
Question 9:
DRAG DROP
Drag and drop the commands from the left onto the purposes on the right to identify issues on a Cisco IOS XE SD-WAN device.
Select and Place:
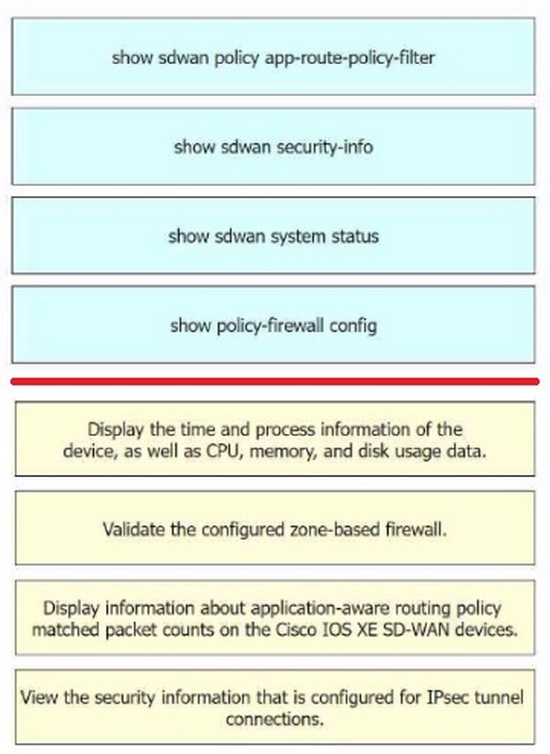
Correct Answer:

Display the time and process information of the device, as well as CPU, memory, and disk usage data. = show sdwan system status Validate the configured zone-based firewall. = show policy-firewall config1 Display information about application-aware routing policy matched packet counts on the Cisco IOS XE SD-WAN devices. = show sdwan policy app-route-policy- filter View the security information that is configured for IPsec tunnel connections. = show sdwan security-info The commands used to identify issues on a Cisco IOS XE SD-WAN device are as follows show sdwan system status: This command is used to display the time and process information of the device, as well as CPU, memory, and disk usage data. show policy-firewall config: This command is used to validate the configured zone-based firewall. show sdwan policy app-route-policy-filter: This command is used to display information about application-aware routing policy matched packet counts on the Cisco IOS XE SD-WAN devices. show sdwan security-info: This command is used to view the security information that is configured for IPsec tunnel connections
References: Cisco IOS XE Catalyst SD-WAN Qualified Command Reference Cisco Catalyst SD-WAN Command Reference Cisco Catalyst SD-WAN Systems and Interfaces Configuration Guide, Cisco IOS XE SD-WAN Tunnel Interface Commands – Cisco
Question 10:
Refer to the exhibit.
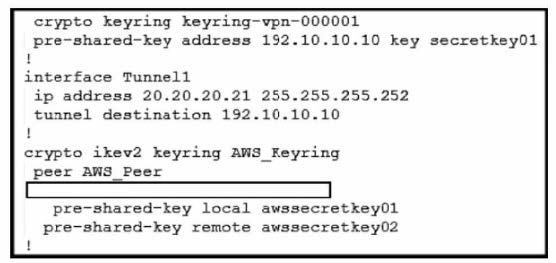
An engineer needs to configure a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and Amazon Web Services (AWS). Which configuration command must be placed in the blank in the code to complete the tunnel configuration?
A. address 20.20.20.21
B. address 192.10.10.10
C. tunnel source 20.20.20.21
D. tunnel source 192.10.10.10
In the given scenario, an engineer is configuring a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and AWS. The correct command to complete the tunnel configuration is “tunnel source 20.20.20.21”. This command specifies the source IP address for the tunnel, which is essential for establishing a secure connection between two endpoints over the internet or another network.
References: Configure IOS-XE Site-to-Site VPN Connection to Amazon Web Services – Cisco Community [Security for VPNs with IPsec Configuration Guide, Cisco IOS XE Release 3S – Config
Question 11:
DRAG DROP
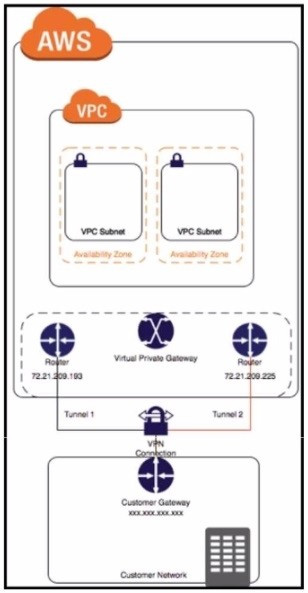
Refer to the exhibit.
Drag and drop the steps from the left onto the order on the right to configure a site-to-site VPN connection between an on-premises Cisco IOS XE router and Amazon Web Services (AWS).
Select and Place:
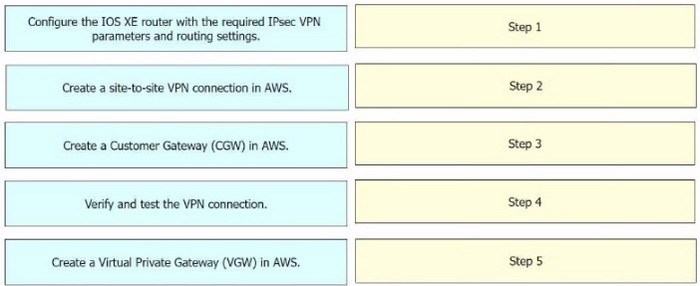
Correct Answer:
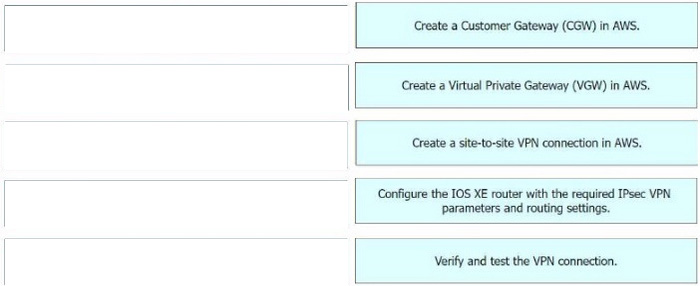
Step 1 = Create a Customer Gateway (CGW) in AWS.
Step 2 = Create a Virtual Private Gateway (VGW) in AWS.
Step 3 = Create a site-to-site VPN connection in AWS.
Step 4 = Configure the IOS XE router with the required IPsec VPN parameters and routing settings.
Step 5 = Verify and test the VPN connection.
The process of configuring a site-to-site VPN connection between an on-premises Cisco IOS XE router and Amazon Web Services (AWS) involves several steps
Create a Customer Gateway (CGW) in AWS: This is the first step where you define the public IP address of your on-premises Cisco IOS XE router in AWS. Create a Virtual Private Gateway (VGW) in AWS: This involves creating a VGW and
attaching it to the VPC in AWS.
Create a site-to-site VPN connection in AWS: After setting up the CGW and VGW, you then create a site-to-site VPN connection in AWS. This involves specifying the CGW, VGW, and the static IP prefixes for your on-premises network.
Configure the IOS XE router with the required IPsec VPN parameters and routing settings: After the AWS side is set up, you configure the on-premises Cisco IOS XE router with the required IPsec VPN parameters and routing settings. Verify
and test the VPN connection: Finally, you verify and test the VPN connection to ensure that it is working correctly.
References:
Configure IOS-XE Site-to-Site VPN Connection to Amazon Web Services – Cisco Community
SD-WAN Configuration Example: Site-to-site (LAN to LAN) IPSec between vEdge and Cisco IOS – Cisco Community
Question 12:
DRAG DROP
An engineer must configure a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router In Controller mode and AWS. The IKE version must be changed from IKEv1to IKEv2 in Cisco vManage. Drag and drop the steps from the left onto the order on the right to complete the configuration.
Select and Place:
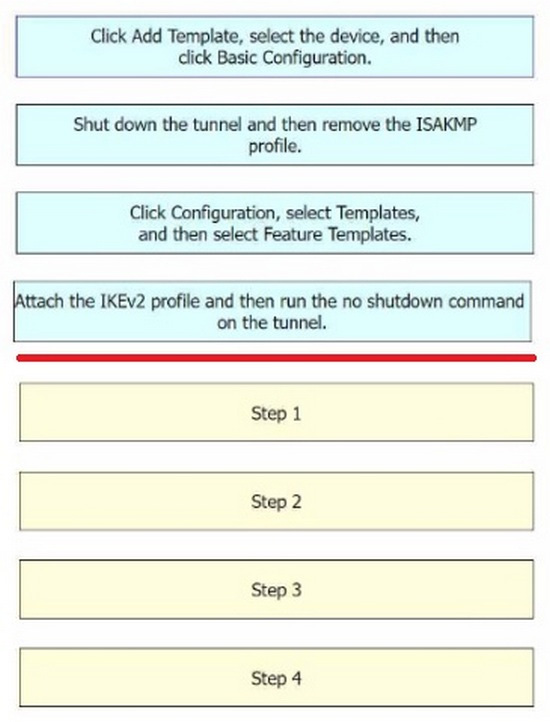
Correct Answer:
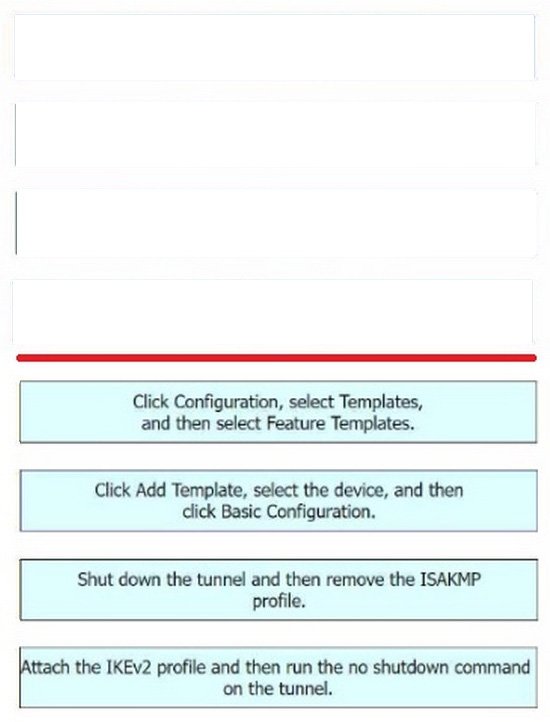
Step 1 = Click Configuration, select Templates, and then select Feature Templates.
Step 2 = Click Add Template, select the device, and then click Basic Configuration.
Step 3 = Shut down the tunnel and then remove the ISAKMP profile.
Step 4 = Attach the IKEv2 profile and then run the no shutdown command on the tunnel.
The process of configuring a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router in Controller mode and AWS, and changing the IKE version from IKEv1 to IKEv2 in Cisco vManage involves several steps123. Click
Configuration, select Templates, and then select Feature Templates: This is the first step where you navigate to the Templates section in the Configuration menu of Cisco vManage1.
Click Add Template, select the device, and then click Basic Configuration: In this step, you add a new template for the device and proceed with the basic configuration.
Shut down the tunnel and then remove the ISAKMP profile: Before changing the IKE version, you need to shut down the existing tunnel and remove the ISAKMP profile that is configured for IKEv12.
Attach the IKEv2 profile and then run the no shutdown command on the tunnel:
Finally, you attach the newly created IKEv2 profile to the tunnel and bring the tunnel back up.
References:
Configuring Internet Key Exchange Version 2 (IKEv2) – Cisco Switch from IKEv1 to IKEv2 on Cisco Routers – Cisco Community Configure IOS-XE Site-to-Site VPN Connection to Amazon Web Services – Cisco Community
Question 13:
Which Microsoft Azure service enables a dedicated and secure connection between an on- premises infrastructure and Azure data centers through a colocation provider?
A. Azure Private Link
B. Azure ExpressRoute
C. Azure Virtual Network
D. Azure Site-to-Site VPN
Azure ExpressRoute is a service that enables a dedicated and secure connection between an on-premises infrastructure and Azure data centers through a colocation provider. A colocation provider is a third-party data center that offers network connectivity services to multiple customers. Azure ExpressRoute allows customers to bypass the public internet and connect directly to Azure services, such as virtual machines, storage, databases, and more. This provides benefits such as lower latency, higher bandwidth, more reliability, and enhanced security. Azure ExpressRoute also supports hybrid scenarios, such as connecting to Office 365, Dynamics 365, and other SaaS applications hosted on Azure. Azure ExpressRoute requires a physical connection between the customer\’s network and the colocation provider\’s network, as well as a logical connection between the customer\’s network and the Azure virtual network. The logical connection is established using a Border Gateway Protocol (BGP) session, which exchanges routing information between the two networks. Azure ExpressRoute supports two models: standard and premium. The standard model offers connectivity to all Azure regionswithin the same geopolitical region, while the premium model offers connectivity to all Azure regions globally, as well as additional features such as increased route limits, global reach, and Microsoft peering.
References: Designing and Implementing Cloud Connectivity (ENCC) v1.0, Learning Plan: Designing and Implementing Cloud Connectivity v1.0 (ENCC 300-440) Exam Prep, ENCC | Designing and Implementing Cloud Connectivity | Netec
Question 14:
Refer to the exhibit.
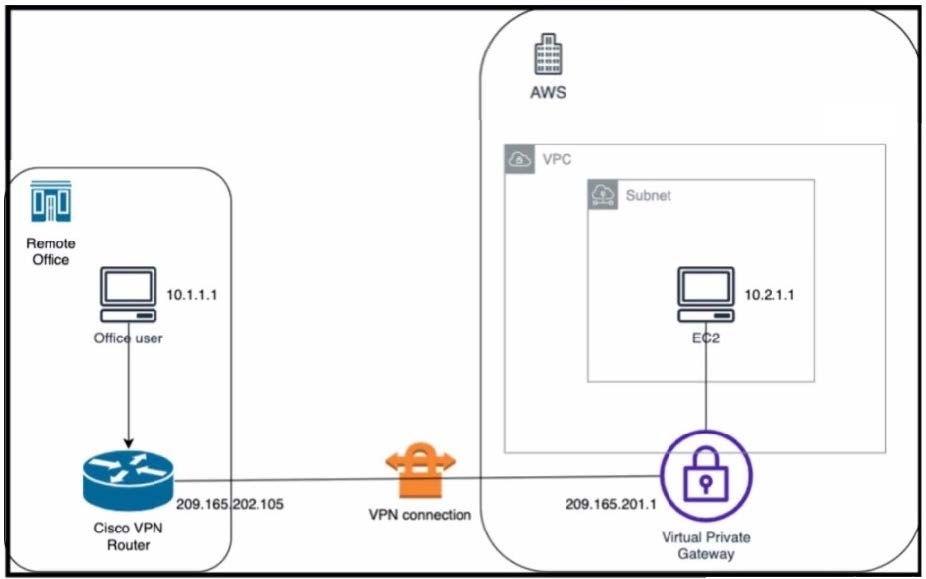
An engineer successfully brings up the site-to-site VPN tunnel between the remote office and the AWS virtual private gateway, and the site-to-site routing works correctly. However, the end-to-end ping between the office user PC and the AWS EC2 instance is not working.
Which two actions diagnose the loss of connectivity? (Choose two.)
A. Check the network security group rules on the host VNET.
B. Check the security group rules for the host VPC.
C. Check the IPsec SA counters.
D. On the Cisco VPN router, configure the IPsec SA to allow ping packets.
E. On the AWS private virtual gateway, configure the IPsec SA to allow ping packets.
The end-to-end ping between the office user PC and the AWS EC2 instance is not working because either the security group rules for the host VPC are blocking the ICMP traffic or the IPsec SA counters are showing errors or drops. To
diagnose the loss of connectivity, the engineer should check both the security group rules and the IPsec SA counters. The network security group rules on the host VNET are not relevant because they apply to Azure, not AWS. The IPsec SA
configuration on the Cisco VPN router and the AWS private virtual gateway are not likely to be the cause of the problem because the site- to-site VPN tunnel is already up and the site-to-site routing works correctly.
References:
Designing and Implementing Cloud Connectivity (ENCC, Track 1 of 5), Module 3:
Configuring IPsec VPN from Cisco IOS XE to AWS, Lesson 3: Verify IPsec VPN Connectivity
Security for VPNs with IPsec Configuration Guide, Cisco IOS XE, Chapter: IPsec VPN Overview, Section: IPsec Security Association AWS Documentation, User Guide for AWS VPN, Section: Security Groups for Your VPC
Question 15:
DRAG DROP
An engineer needs to configure enhanced policy-based routing (ePBR) for IPv4 by using Cisco vManage. Drag and drop the steps from the left onto the order on the right to complete the configuration of the ePBR using the CLI add-on template.
Select and Place:
Correct Answer:
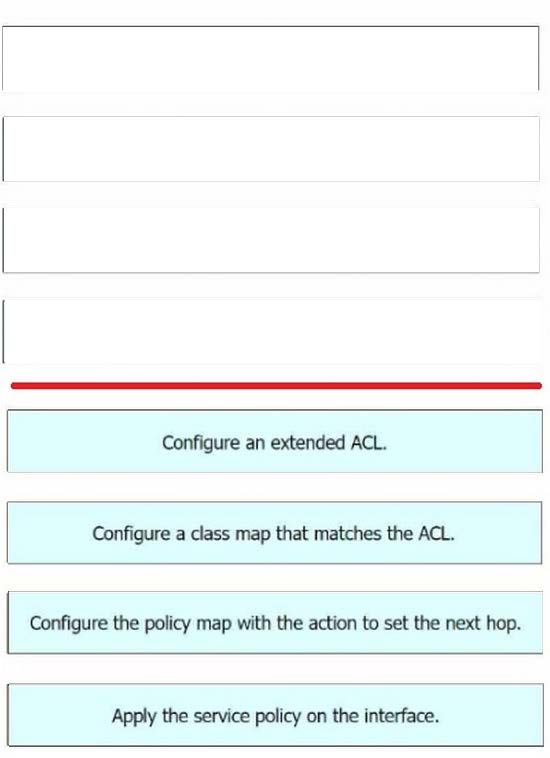
Enhanced Policy-Based Routing (ePBR) is used to direct packets that arrive at an interface to a specified next-hop. It is very useful in managing a large number of configured access lists more efficiently. In ePBR, the router drops the traffic packets if the next hop configured in the PBR policy is not reachable. To avoid packet loss in such scenarios, you must configure multiple next hops for each access control entry. Here are the steps to configure ePBR for IPv4 using Cisco vManage: Configure an extended ACL: This step involves defining the network or the host. For example, you can permit IPv4 traffic from any source to specific hosts. Configure a class map that matches the ACL: Class maps match the parameters in the ACLs. For instance, you can create a class map of type traffic and match it with the previously created ACL. Configure the policy map with the action to set the next hop: Policy maps with ePBR then take detailed actions based on the set statements configured. You can configure an ePBR policy map with the class map and set the next hop. Apply the service policy on the interface: Finally, you apply the ePBR policy map to the interface. For example, you can apply the policy map to a GigabitEthernet interface. References : Implementing Enhanced Policy Based Routing – Cisco Cisco Catalyst SD-WAN Policies Configuration Guide, Cisco IOS XE How to configure PBR – Cisco Community
…
Cisco 300-440 exam questions answers
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| B | B | B | C | B | C | IMAGE | A | IMAGE | C | IMAGE | IMAGE | B | BC | IMAGE |
Summarize
Cisco 300-440 ENCC dumps contains 38 latest exam questions and answers. https://www.leads4pass.com/300-440.html It also provides two practice tools, PDF and VCE, to ensure that you pass the exam 100% successfully. And 300-440 ENCC dumps are updated throughout the year, you can download and use them at any time to ensure real-time effectiveness.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

