Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Valid Cisco 350-201 questions shared by Pass4itsure for helping to pass the Cisco 350-201 exam! Get the newest Pass4itsure Cisco 350-201 exam dumps with VCE and PDF here: https://www.pass4itsure.com/350-201.html (102 Q&As Dumps).
[Free PDF] Cisco350-201 pdf Q&As https://drive.google.com/file/d/1suzCB9m6Y2uf5CUGUBCQhpnmyVnR5X-F/view?usp=sharing
Suitable for 350-201 complete Cisco learning pathway
The content is rich and diverse, and learning will not become boring. You can learn in multiple ways through the Cisco 350-201 exam.
- Download
- Answer practice questions, the actual Cisco 350-201 test
Cisco 350-201 Performing CyberOps Using Cisco Security Technologies (CBRCOR)
Free Cisco 350-201 dumps download
[PDF] Free Cisco 350-201 dumps pdf download https://drive.google.com/file/d/1suzCB9m6Y2uf5CUGUBCQhpnmyVnR5X-F/view?usp=sharing
Pass4itsure offers the latest Cisco 350-201 practice test free of charge 1-13
QUESTION 1
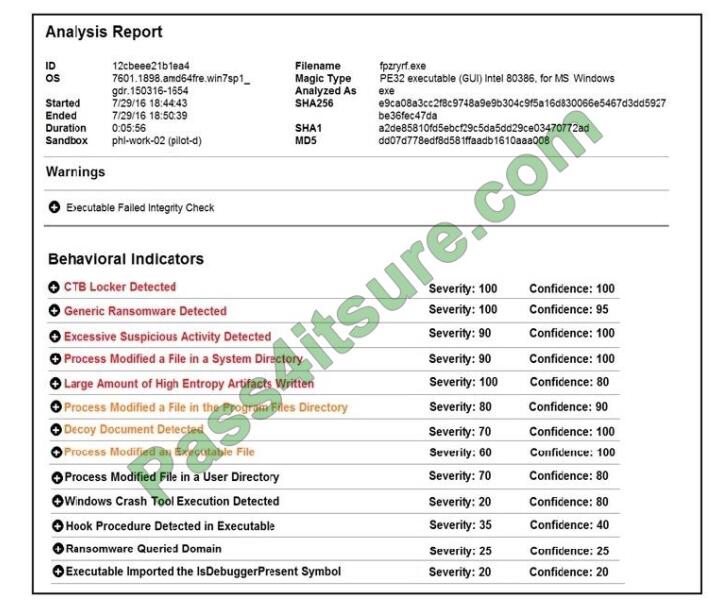
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted
a low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded from this report?
A. The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the
scores do not indicate the likelihood of malicious ransomware.
B. The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the
scores are high and do not indicate the likelihood of malicious ransomware.
C. The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are
high and indicate the likelihood that malicious ransomware has been detected.
D. The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are
low and indicate the likelihood that malicious ransomware has been detected.
Correct Answer: C
QUESTION 2
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident
response team. Which actions should be taken at this step in the incident response workflow?
A. Classify the criticality of the information, research the attacker\\’s motives, and identify missing patches
B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation
plan
Correct Answer: B
QUESTION 3
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having
the names of the 3 destination countries and the user\\’s working hours, what must the analyst do next to detect an
abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
Correct Answer: D
QUESTION 4
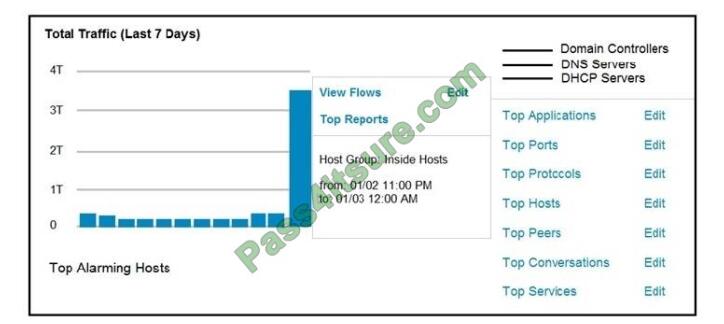
Refer to the exhibit. An engineer notices a significant anomaly in the traffic in one of the host groups in Cisco Secure
Network Analytics (Stealthwatch) and must analyze the top data transmissions. Which tool accomplishes this task?
A. Top Peers
B. Top Hosts
C. Top Conversations
D. Top Ports
Correct Answer: B
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2018/pdf/BRKSEC-3014.pdf
QUESTION 5
What is a limitation of cyber security risk insurance?
A. It does not cover the costs to restore stolen identities as a result of a cyber attack
B. It does not cover the costs to hire forensics experts to analyze the cyber attack
C. It does not cover the costs of damage done by third parties as a result of a cyber attack
D. It does not cover the costs to hire a public relations company to help deal with a cyber attack
Correct Answer: A
Reference: https://tplinsurance.com/products/cyber-risk-insurance/
QUESTION 6
An analyst is alerted for a malicious file hash. After analysis, the analyst determined that an internal workstation is
communicating over port 80 with an external server and that the file hash is associated with Duqu malware. Which
tactics, techniques, and procedures align with this analysis?
A. Command and Control, Application Layer Protocol, Duqu
B. Discovery, Remote Services: SMB/Windows Admin Shares, Duqu
C. Lateral Movement, Remote Services: SMB/Windows Admin Shares, Duqu
D. Discovery, System Network Configuration Discovery, Duqu
Correct Answer: A
QUESTION 7
What is the purpose of hardening systems?
A. to securely configure machines to limit the attack surface
B. to create the logic that triggers alerts when anomalies occur
C. to identify vulnerabilities within an operating system
D. to analyze attacks to identify threat actors and points of entry
Correct Answer: A
QUESTION 8
Refer to the exhibit. What is occurring in this packet capture?
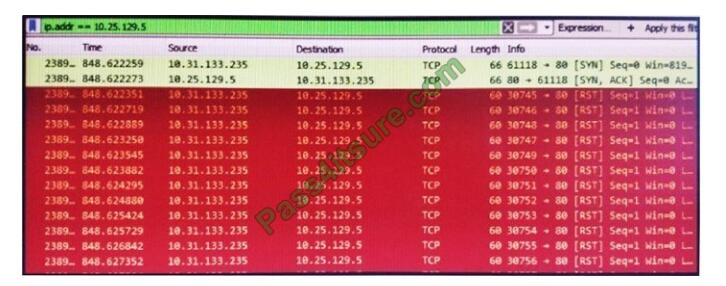
A. TCP port scan
B. TCP flood
C. DNS flood
D. DNS tunneling
Correct Answer: B
QUESTION 9
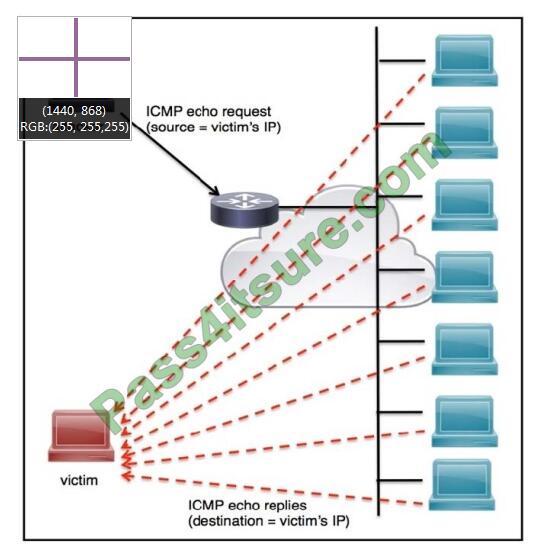
Refer to the exhibit. An engineer must tune the Cisco IOS device to mitigate an attack that is broadcasting a large
number of ICMP packets. The attack is sending the victim\\’s spoofed source IP to a network using an IP broadcast
address that causes devices in the network to respond back to the source IP address.
Which action does the engineer recommend?
A. Use command ip verify reverse-path interface
B. Use global configuration command service tcp-keepalives-out
C. Use subinterface command no ip directed-broadcast
D. Use logging trap 6
Correct Answer: A
Reference: https://www.ccexpert.us/pix-firewall/ip-verify-reversepath-command.html
QUESTION 10
A customer is using a central device to manage network devices over SNMPv2. A remote attacker caused a denial of
service condition and can trigger this vulnerability by issuing a GET request for the ciscoFlashMIB OID on an affected
device.
Which should be disabled to resolve the issue?
A. SNMPv2
B. TCP small services
C. port UDP 161 and 162
D. UDP small services
Correct Answer: A
Reference: https://nvd.nist.gov/vuln/detail/CVE-2018-0161
QUESTION 11
Employees report computer system crashes within the same week. An analyst is investigating one of the computers that
crashed and discovers multiple shortcuts in the system\\’s startup folder. It appears that the shortcuts redirect users to
malicious URLs.
What is the next step the engineer should take to investigate this case?
A. Remove the shortcut files
B. Check the audit logs
C. Identify affected systems
D. Investigate the malicious URLs
Correct Answer: C
QUESTION 12
How is a SIEM tool used?
A. To collect security data from authentication failures and cyber attacks and forward it for analysis
B. To search and compare security data against acceptance standards and generate reports for analysis
C. To compare security alerts against configured scenarios and trigger system responses
D. To collect and analyze security data from network devices and servers and produce alerts
Correct Answer: D
Reference: https://www.varonis.com/blog/what-is-siem/
QUESTION 13
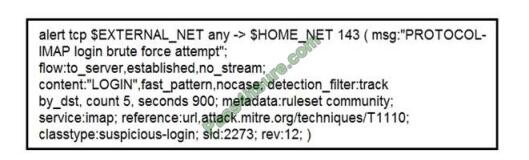
Refer to the exhibit. IDS is producing an increased amount of false positive events about brute force attempts on the
organization\\’s mail server. How should the Snort rule be modified to improve performance?
A. Block list of internal IPs from the rule
B. Change the rule content match to case sensitive
C. Set the rule to track the source IP
D. Tune the count and seconds threshold of the rule
Correct Answer: B
Pass4itsure Cisco exam dumps discount code share

Summarize:
[Q1-Q13] Free Cisco 350-201 pdf download https://drive.google.com/file/d/1suzCB9m6Y2uf5CUGUBCQhpnmyVnR5X-F/view?usp=sharing
Share all the resources: Latest Cisco 350-201 practice questions, latest Cisco 350-201 pdf dumps. The latest updated Cisco 350-201 dumps https://www.pass4itsure.com/350-201.html Study hard and practices a lot. This will help you prepare for the Cisco 350-201 exam. Good luck!
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

