Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Get the latest Cisco 200-201 exam dumps to help you prepare for the exam easily, you need more practice and practice every day. Following are some new Cisco 200-201 exam questions. Complete Cisco 200-201 exam dumps questions and answers: https://www.pass4itsure.com/200-201.html (PDF + VCE).
[Free 200-201 practice test] Cisco 200-201 exam questions answers q1-q15
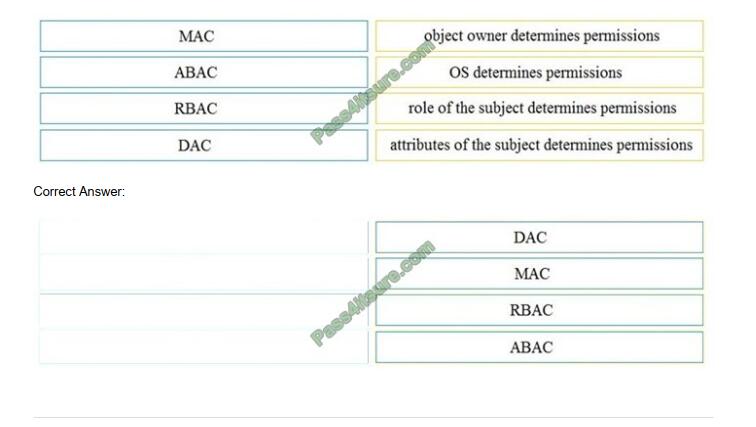
QUESTION 1
DRAG DROP
Drag and drop the access control models from the left onto the correct descriptions on the right.
Select and Place:
QUESTION 2
Which two elements are used for profiling a network? (Choose two.)
A. session duration
B. total throughput
C. running processes
D. listening ports
E. OS fingerprint
Correct Answer: DE
QUESTION 3
At which layer is deep packet inspection investigated on a firewall?
A. internet
B. transport
C. application
D. data link
Correct Answer: C
QUESTION 4
DRAG DROP
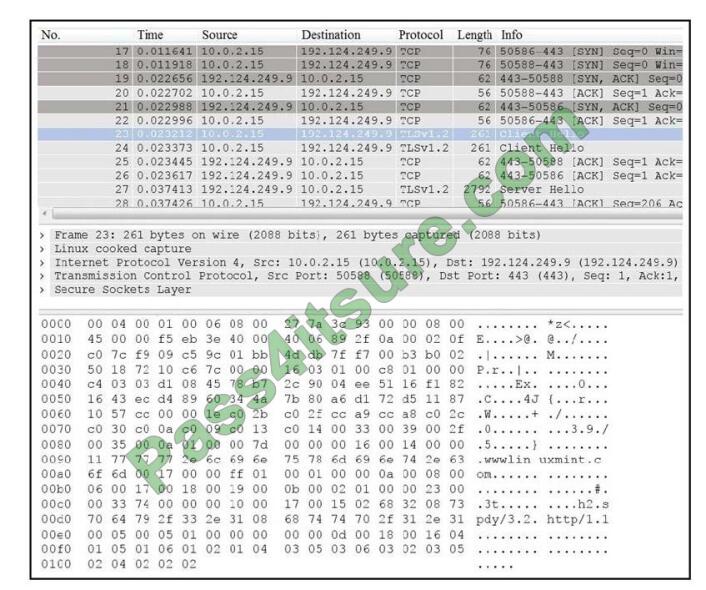
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
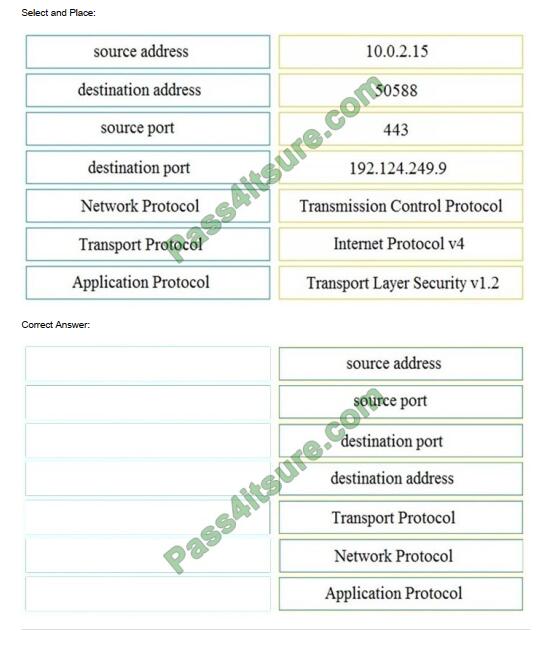
QUESTION 5
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
A. confidentiality, identity, and authorization
B. confidentiality, integrity, and authorization
C. confidentiality, identity, and availability
D. confidentiality, integrity, and availability
Correct Answer: D
QUESTION 6
What is the difference between an attack vector and attack surface?
A. An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies
vulnerabilities that are independent of user actions.
B. An attack vector identifies components that can be exploited; and an attack surface identifies the potential path an
attack can take to penetrate the network.
C. An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which
attacks are possible with these vulnerabilities.
D. An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using
several methods against the identified vulnerabilities.
Correct Answer: C
QUESTION 7
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company\\’s corporate PCs.
Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
A. application whitelisting/blacklisting
B. network NGFW
C. host-based IDS
D. antivirus/antispyware software
Correct Answer: A
QUESTION 8
What is a purpose of a vulnerability management framework?
A. identifies, removes, and mitigates system vulnerabilities
B. detects and removes vulnerabilities in source code
C. conducts vulnerability scans on the network
D. manages a list of reported vulnerabilities
Correct Answer: A
QUESTION 9
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
A. The average time the SOC takes to register and assign the incident.
B. The total incident escalations per week.
C. The average time the SOC takes to detect and resolve the incident.
D. The total incident escalations per month.
Correct Answer: C
QUESTION 10
What is the relationship between a vulnerability and a threat?
A. A threat exploits a vulnerability
B. A vulnerability is a calculation of the potential loss caused by a threat
C. A vulnerability exploits a threat
D. A threat is a calculation of the potential loss caused by a vulnerability
Correct Answer: A
QUESTION 11
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Untampered images are used in the security investigation process
B. Tampered images are used in the security investigation process
C. The image is tampered if the stored hash and the computed hash match
D. Tampered images are used in the incident recovery process
E. The image is untampered if the stored hash and the computed hash match
Correct Answer: BE
QUESTION 12
An engineer discovered a breach, identified the threat\\’s entry point, and removed access. The engineer was able to
identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step
the engineer should take according to the NIST SP 800-61 Incident handling guide?
A. Recover from the threat.
B. Analyze the threat.
C. Identify lessons learned from the threat.
D. Reduce the probability of similar threats.
Correct Answer: B
QUESTION 13
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the
same data center were transferred to a competitor. Which type of evidence is this?
A. best evidence
B. prima facie evidence
C. indirect evidence
D. physical evidence
Correct Answer: C
QUESTION 14
What is the practice of giving an employee access to only the resources needed to accomplish their job?
A. principle of least privilege
B. organizational separation
C. separation of duties
D. need to know principle
Correct Answer: A
QUESTION 15
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its
integrity?
A. examination
B. investigation
C. collection
D. reporting
Correct Answer: C
[Free 200-201 PDF] Cisco 200-201 dumps pdf download
free 200-201 dumps pdf https://drive.google.com/file/d/13zAYB136wOM6aF_Bhk0y84vZ3FmkyvAH/view?usp=sharing
Pass4itSure provides updated Cisco 200-201 dumps as 200-201 practice test and 200-201 pdf. 100% same braindumps with actual 200-201 exam! Please click https://www.pass4itsure.com/200-201.html (Q&As: 153). Trust Pass4itSure and start preparing, good luck!
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

